The 5 Fundamentals of a Successful Cybersecurity Program
Published: Oct 28, 2021
Last Updated: Nov 25, 2025
We all know that cybercriminals are now a thing.
Most of our lives are on the Internet now, so it makes sense that nefarious characters have made their way there too. This new reality has created a new dependency on cybersecurity both personally and professionally, and if your business is anything like us at Schellman, your #1 priority throughout everything is client trust.
These days, cyber defenses are key to that, but implementing the necessary protections is definitely easier said than done sometimes. There are so many different ways a bad actor can attack you and your systems—phishing, ransomware, cracking passwords, DDoS, among others.
It’s a lot.
So how do you know you’re doing what it takes to defend against all these attacks, to prevent devastating breaches, and to keep your customers reassured that they made the right decision in trusting you?
The Internet may be a vast and often treacherous place, but there are still several good ways to shore up your approach to information security. If you’re now wondering about your own potential red flags—don’t worry, because spotting vulnerabilities is a specialty of ours. Schellman exclusively dedicates a team to penetrating client systems in search of weak spots, and we’ve seen quite the range as we’re asked to find things ripe for strengthening.
But no matter what services you provide, or what systems you’re using to support them, we’ve identified some fundamental things that you should do to adequately protect data for the long term.
So, here are five things you should consider when building a comprehensive cybersecurity program. No matter if you’re just kickstarting your own for a new business, or if you’re just wanting to feel good about the established program you already have, taking action in these areas within your organization will put you on the road to strong data protection.
1. Cybersecurity Must Be Everyone’s Problem
A good first step is to engage this as an ‘everybody’ responsibility—that means one that is shared throughout all aspects of your organization, not just very specifically the IT guys who deal with the computers.
In reality, cybersecurity should influence how organizations are structured, staffed, and operationalized from top to bottom. A good cybersecurity program maintains sufficient administrative, technical, and physical controls that work synergistically to identify and defend our data.
Put like that, it sounds like a ton of work, I know, but in implementing a more holistic approach like this, it really does ensure that all your resources are focused and engaged in a more meaningful way.
Still, for that to really work, you need to not only educate your employees on what kind of attacks to be wary of and what they look like, but you also need a set procedure they know to follow should they spot something suspicious.
For example:
- What information must be reported, to whom and by when? (client, corporate, agency)
- How is this information to be shared?
- What information can or should be shared with law enforcement officers (particularly, in the case of sensitive and/or protected data)?
- Are there specific actions which must be taken to support claims under the organization’s cybersecurity insurance policy?
If these are questions you already know the answer to off the top of your head, then great. But if you find yourself a little murky on the details, or you’re blanking on all of it, now is the time to clear things up—not just for your sake, but for the rest of your personnel too. With everyone on the same, educated page, the sensitive information in your charge is that much safer.
2. It’s 11 P.M. on a School Night - Do You Know Where Your Data Is?
That’s human awareness out of the way—now let’s talk about more technical prudence. You need to understand the nature of your data and where it resides—both in physical and digital format. More specifically:
- How is this data is received, stored, processed and/or transmitted within your enclaves?
- Are there outside expectations (legal, regulatory and/or contractual) with respect to the protection of this information?
- And finally – which users, devices, (sub)processes and/or services have access to this data and how is access authenticated and preserved?
That’s three questions that probably have very complicated answers, and creating a data flow diagram may help to answer some.
How? At least to start, it can serve to visualize the flow of information across your network, which can make it easier in trying to pin everything down. Plus, depending on how detailed you want to get with it, a data flow chart can also help you:
- Categorize the data, associated protections, and special handling
- Identifying all connected devices which may potentially be exploited (e.g., switches or routers)
- Establish where residual data may reside (printers, scanners, etc.).
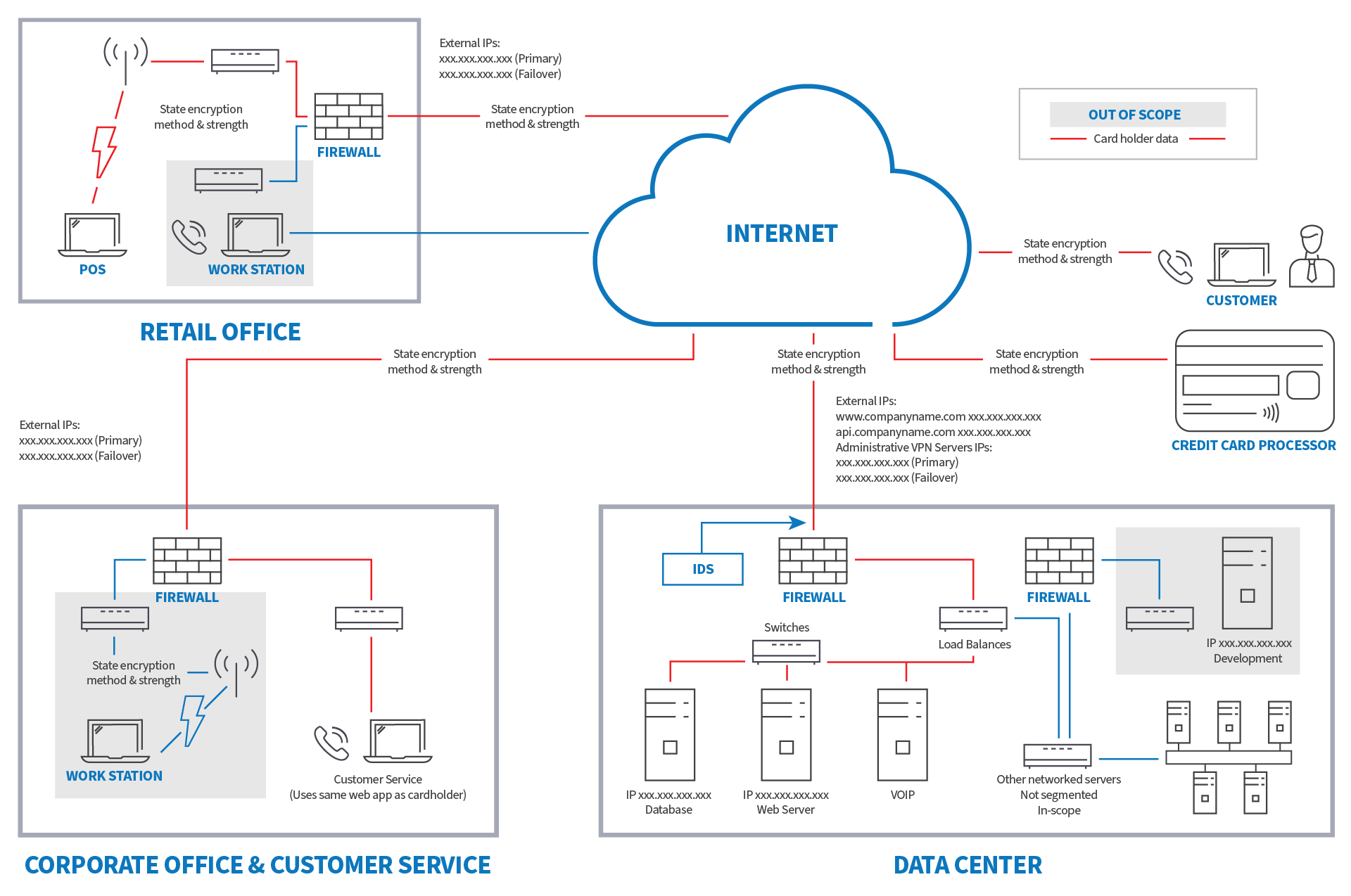
1 Example Data Flow Diagram for a fictional organization
3. Prioritize Patch Management
One thing we all have working for us is that hackers are largely consistent in their approach using common vulnerabilities and exposures (CVEs) to determine weaknesses within our information systems and platforms. The bad news is that there are many sites that host this type of information, including the Google Hacking Database (GHDB), which currently provides a real-time reporting of these CVEs and the methods and/or means to exploit. This is where a consistent and timely patch management capability comes in—one that continually scans for and responds to these types of threats.
There are a variety of cost-effective tools which may help to automate and further integrate this process – for example, NinjaRMM and other services. Having said this, buyer beware – just like your internal tools, these tools and services are only as good as they are configured and maintained, so the onus remains on you and your personnel to stay aware and maintain implementation.
4. Make Sure to Have a Plan B
You’ve probably heard this before, but it’s integral to implement a solid data backup and recovery process. What you may not have heard is that it’s just as important to support that process through frequent testing so as to validate its efficacy and efficiency. What’s more, you need to incorporate after action reviews to discuss potential improvements.
Do regular tests and then ask yourselves, what went well and what could we have done better?
But it’s not just about a Plan B for when things go wrong. You need to have more than just the minimum in more capacities. For instance, enhanced monitoring may help to serve as an early warning indicator, providing those critical extra moments to identify, isolate and respond to threat indicators while you gather resources for the real fight.
Other things to consider:
- Multi-factor authentication for access to data
- Restrictions on the use of personally owned devices
- A strong password policy (check out that which is defined by NIST SP 800-63 for tips on that)
- Timely provisioning/decommissioning of devices, accounts, and other assets when necessary
5. Control Access on All Fronts
Because the human element oftentimes plays the largest role in a data breach, so much of data protection can hinge on controlling exactly who has access to what, be it data coming into your organization, or which users can float where within the network. Some suggestions for access control:
- Use antivirus at all times. Set your software to automatically scan emails and flash drives.
- Segment networks. Segment internal networks to prevent malware from proliferating among potential target systems.
- Block access to potentially malicious web resources. Use products or services that block access to server names, IP addresses, or ports and protocols that are known to be malicious or suspected to be indicators of malicious system activity.
- Allow only authorized apps. Configure operating systems and/or third-party software to run only authorized applications.
- Use standard user accounts versus accounts with administrative privileges whenever possible.
- Assign and manage credential authorization for all enterprise assets and software, and periodically verify that each account has the appropriate access only.
BONUS: Invest in Compliance
Obviously, there’s a lot you can do internally to build up your defenses, and you’ve got plenty of directives now for things to implement or update within your organization in order to strengthen your defenses. But even after all that, sometimes it can make for an enormous boost to find outside validation that you’re doing all the things you need to in order to protect your customers.
That’s where assessors like Schellman can come in and evaluate the different controls and steps you’ve taken—there are so many different examinations and certifications available depending on each organization’s needs and the type of data being handled.
As one of our current clients at AliveCor says, “it…brings in that extra pair of eyes you don’t otherwise have to say, ‘this is where we are lacking,’ and ‘this is where we are looking good’…having a third party come in is the best way…to reduce our risk, which is the entire point.”
But no matter what you choose to do, be it shoring up your defense internally, investing in a third-party audit, or even self-assessing yourself to a security standard, in taking these steps towards a robust cybersecurity program, you can help prevent your own exploitation, ensuring your customers and prospects remain confident in your product.
Should you be interested in seeking that extra validation—both for internal confidence as well as reassurance for your customers, feel free to contact us.
About Schellman
Schellman is a leading provider of attestation and compliance services. We are the only company in the world that is a CPA firm, a globally licensed PCI Qualified Security Assessor, an ISO Certification Body, HITRUST CSF Assessor, a FedRAMP 3PAO, and most recently, an APEC Accountability Agent. Renowned for expertise tempered by practical experience, Schellman's professionals provide superior client service balanced by steadfast independence. Our approach builds successful, long-term relationships and allows our clients to achieve multiple compliance objectives through a single third-party assessor.



