Burp Suite Certified Practitioner: Exam Review
Published: Feb 11, 2022
Last Updated: Jan 19, 2024
Benjamin Franklin once said, “an investment in knowledge always pays the best interest.”
A little more current than Mr. Franklin’s time, PortSwigger recently provided their own opportunity to “invest in knowledge” through their release of the Burp Suite Certified Practitioner certification. This is obtained by completing a technical exam that is intended to accompany the Web Security Academy—Portswigger’s official training platform designed to teach a wide variety of application security concepts with Burp Suite.
Application security is a core focus on our Pen Test team, which means we work heavily with Burp Suite. The content in the Web Security Academy is well renowned for its relevancy and practical approach, so I was very interested in the opportunity to expand my expertise through this exam.
What follows in this article is my experience with the Academy and the exam. Having now obtained certification myself, I wanted to offer my perspective to help other security professionals decide more ably if it’s really right for you.
What Does the Web Security Academy Offer?
At the time of writing this, Portswigger’s Web Security Academy consists of 211 different lab challenges on intentionally vulnerable web applications. These applications are organized into multiple categories based on vulnerability such as Cross-Site Scripting (XSS) or HTTP Request Smuggling.
The labs vary in difficulty, ranging from “Apprentice” (50 total), “Practitioner” (131 total), and “Expert” (30 total) respectively. Each section also features accompanying articles that explain what the overall security issues are and how they can be exploited. The learning material is all top-notch and based on relevant content that, in a lot of instances, I found would directly translate to real world findings during live application penetration tests.
What’s more is, the Web Security Academy content is completely free. Even if you’re not planning to take the Burp Suite Certified Practitioner Exam, it’s well worth your time for the knowledge gleaned alone—everyone in the information security community would gain something of value.
But if you are planning on taking the exam, there’s a few things to consider which include:
- Paying a reasonable $99 fee; and
- Having a Burp Professional license. (This is required to access some of the features you’ll need.)
What can you expect from the experience? Let’s break it down.
Preparation for the Burp Suite Certified Practitioner Exam
If you’re planning to take this exam, PortSwigger recommends you complete all the “Apprentice” and “Practitioner” level labs. Following this, you should take their practice exam, which will simulate the type of vulnerable applications—goals and all—that you will face when you sit for the actual exam.
However much milage you rack up preparing will vary depending on what type of labs you focus on. To be the most comfortable going into the exam, definitely complete all their recommended labs. But depending on your current experience that may not be entirely necessary—prior to my own exam attempt, here’s where I stood:
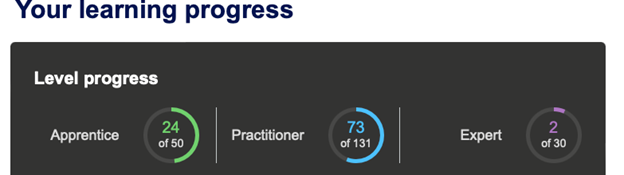
Given the short amount of time you are given for the exam, I chose to personally focus on areas where I felt the least confident performing quick exploitation.
As I’ll note in more detail later, exploitation, especially against a “simulated victim,” is a core component of the exam. If you want to skip around like I did, just make sure you’re definitely familiar with this part of the labs.
I also found that it wasn’t easy to jump feet first into the practice exam after lab training. It wasn’t always clear what they were asking you to accomplish, so to be sure you know what your goals are. Give the “What The Exam Involves” section a close read for some useful tips.
To break it down further, know this—each vulnerable application consists of the following three stages:
- Gain initial access to any user account.
- Escalate privileges and access the admin interface.
- Read the contents of the “/home/carlos/secret” file.
These stages are expected to be exploited in order. Know now that it’s a waste of time trying to directly go to the admin interface without some type of initial account access. Similarly, attempting to read the “secret” file is pointless without access to admin functionality.
In the end, I was able to pass the practice exam after a few tries. My attempts gave me an understanding on what I needed to focus on, and exploitation was a big part of that.
It may go without saying, but passing the practice exam is essential to performing well on the actual exam. It confirms that you understand not only the type of attacks that are important, but also the quirks that come with Web Security Academy labs, such as performing exploits against the simulated victim.
The practice exam also has unlimited retakes, so take your time and focus on understanding the process as much as possible.
What to Expect from the Burp Suite Certified Practitioner Exam
Once you’ve exploited your way through the labs, you’re ready for the real thing.
The exam is “open book,” so you’ll be free to use any features in Burp Pro, such as automated scanning and extensions, in addition to any notes you might have, online resources, third-party tools, etc.
What’s the process like?
- After a short proctoring exercise via Examity, the exam starts with four hours on the clock. If you’ve completed the recommended training like I said, the way the exam is presented should seem straight forward.
- You will be given access to two applications, each requiring you to exploit your way through the three different stages.
- There have been some reports of technical issues encountered during the exam, but I personally didn’t experience any problems. (I did face some odd behavior with the simulated victim during my time in the labs, but everything went smoothly during my exam attempt.)
- Each exam application is generated under a randomized subdomain. While it’ll look familiar if you did the labs or the practice exam, it still might present a small problem as the similarities between applications can make it confusing to switch back and forth.
- If this is an issue for you, try focusing on one application at a time—only switch over to review the differences between the two. This might also help you find where to focus your attention.
3 Tips for the Burp Suite Certified Practitioner Exam
1. Understand How to Exploit (Specifically)
Like I said before, exploitation is fundamental to success. It’s required to progress through each stage and each application is configured with a “simulated victim” that can only be exploited using an exploitation server they provide. Minimal effort here, like say, performing client-side attacks against yourself, will not gain you any progress.
2. Take a Strategic Approach
This is the best advice I can give.
- At the time of my exam attempt, the labs were organized into twenty-two different categories. To pass the exam, you need to balance thoroughness and speed—not only in identifying the issues under these categories, but also to efficiently exploit them to obtain the access needed to progress through each stage.
- My suggestion? Think about the stages and the end-goal, then review the lab categories and map out what security issues are relevant for each stage. The practice exam should give you an idea on the type of exploitation you need to be prepared to perform.
3. Be Ready for Randomization
During my time with the practice exam, I noticed parameters were randomized with each attempt, and in fact, PortSwigger themselves confirmed that the actual challenges you will face in each stage of the exam are random.
What does that mean?
- It’s not feasible to “brute force” your way through it by getting the exact same challenges after multiple attempts.
- You can’t just copy and paste payloads from your previous attempt even if you do get lucky and run into the same challenge twice.
Randomization is a great idea for an exam environment in that it enforces the reality that, to successfully pass, you need to prove in-depth knowledge across a broad range of application security issues. But it can also render the applications a little “nonsensical” from a development standpoint—they come off more CTF-esque rather than as a “real-world” application penetration test. Still, this is what you’ll face during the exam, so just be aware.
Finishing the Burp Suite Certified Practitioner Exam
While I did find the exam challenging, I struggled the most with exploitation on the first stage for each application. Technically, you only have 40 minutes per challenge and it’s not difficult to see how one trip down a rabbit hole could lead to failure. But the pressure made those challenges that much more rewarding to solve, honestly.
Once you complete both applications, there doesn’t appear to be a way to end the exam early, so you need to wait for the time to run out before you get the official confirmation that you’ve completed the “technical” portion of the exam. Also, for those wondering, there’s no report required.
After a few days, the team at PortSwigger will verify your results and post your certification to the “My Account” section in your PortSwigger account. The certification is good for five years.

Overall, I enjoyed my time with the exam and plan to revisit the lab challenges that I skipped over at some point. This was my first technical exam since I passed the Offensive Security Certified Professional (OSCP) certification a few years ago and it was a similar experience—just with a sole focus on application security this time.
For someone that works extensively with Burp Suite like I do at Schellman, this entire process has elevated my knowledge and experience with a variety of application security concepts to a new level. Whether or not you do opt to take this exam, read our other articles on Burp Suite. They may not yield certifications, but they can help expand your expertise:
About Cory Rey
Cory Rey is a Lead Penetration Tester at Schellman where he plays a key role in advancing the firm’s offensive security capabilities, including spearheading the development of its AI Red Team service line. Focused on performing penetration tests for leading cloud service providers, he now extends his expertise to identifying and exploiting vulnerabilities in Generative AI systems—areas often overlooked by traditional security assessments. With a strong foundation in Application Security, Cory has a proven track record of uncovering complex security flaws across diverse environments.




