Do You Need a Ransomware Preparedness Assessment?
Published: Mar 29, 2022
Last Updated: Jan 19, 2024
A while ago, we posed this question, “Do You Need a Ransomware Preparedness Assessment?”
Even back then, the answer was a resounding “yes.” But since we originally published this, the reality of ransomware and the need to prepare has become more urgent than ever.
Because now, insurers are rapidly reviewing and evolving their cyber coverage, exclusions, and pricing. Recent months have seen cyber insurance prices surge as insurers continue to pass on the cost of ransomware claims. Given this new uncertainty in the industry—thanks to the fact that the liability associated with a breach is an increasingly daunting and moving target—some organizations are even choosing to rebuff coverage altogether, opting to just shoulder the risk themselves.
Whether that’s the right call for your organization is outside of our area of expertise. But there’s no denying that this hot potato issue has become white hot. Given this combination of skyrocketing criminal activity, an expanded regulatory environment, and insurers continuing to stoke the flame with rising premiums, we decided that it might be helpful to repost our original article (below).
What’s more, in an earnest effort to add immediate value, you can gain free access to our guidance on the CISA Cyber Security Evaluation Tool (CSET®).
While CSET® is already a valuable free resource, we believe that our contextual overview can clarify the spirit of the questions, point out some common pitfalls, and provide insight into specific controls we’ve seen leveraged effectively as our clients continue to improve their ability to thwart hackers.
After reviewing the below article and/or accessing our CSET® Ransomware Guide, please know that Schellman’s team of experts is ready to help.
Simply contact us and we’ll be happy to answer your questions and discuss whether a Ransomware Readiness Assessment is the right next step.
+++
American author Stewart Brand said, “once a new technology rolls over you, if you’re not part of the steamroller, you’re part of the road.”
He’s not wrong, but his words also ring particularly true when considering cyber threats as well. Falling behind on the latest technological advancements is one thing, but falling victim to an attack that means financial and reputational loss is entirely another.
While there are many different vulnerabilities and attack vectors, ransomware has been a wake-up call for many regarding the variety of threats that persist in the cybersecurity space. In recent history, we’ve seen many shocking things, including:
- Multi-million-dollar ransoms
- Involvement of the U.S. Secret Service and FBI on ransomware attacks
- Public disclosure of stolen data by ransomware gangs
All these consequences are often worst-case scenarios for most organizations. Ransomware represents such a persistent and devastating threat that it has caught the attention of executive leadership teams who are asking a basic question of their business: “are we prepared against ransomware?”
At Schellman, a cybersecurity and compliance firm, we often speak with organizations that have these concerns. This presence we have within the IT audit space—including our work with cybersecurity standards—has put us in a position to help you answer that question.
We’ve put together an assessment that, if used, can help you determine whether your organization is adequately prepared against a potential ransomware attack.
We understand that each organization will have different use cases and may need a tailored approach to their specific challenges. This is exactly why our offering is broken into tiers that will require varying levels of your investment.
So, read on to understand exactly what ransomware is and how our new assessment can help you determine your preparedness against it. Afterward, you’ll know of at least one option that can help ensure you aren’t “steamrolled” and whether it’s right for you.
What is Ransomware?
Before we dive into how we can help you protect yourself, let’s establish exactly what we can help you defend against.
The dictionary defines ransomware as “a type of malicious software designed to block access to a computer system until a sum of money is paid.” While technically accurate, what makes this malware so uniquely problematic among cybercrime is the fact that it forces you—the organization theoretically being attacked—to become complicit in the fact.
Not only that, but because history has demonstrated that these attacks do work, they’re more likely to keep happening. In October 2021, the NSA stated that they expect the United States to face ransomware attacks every single day for the next five years, and other reports have found that, collectively, ransomware costs are projected to keep climbing into the hundreds of billions over the next 20 years.
That’s likely because in their success securing ransoms, cyber attackers are also working towards new models for their malware—that elevation in sophistication by criminals must be mirrored by organizations in safeguarding their critical assets and valuable data. Luckily, elevating your cybersecurity sophistication is what we can help you do.
Are You Secure Against Ransomware?
Find Out.
More specifically, Schellman can help you through a tiered assessment that can begin to answer the question of whether you’re prepared for a ransomware incident. We’re calling it a Ransomware Preparedness Assessment, and we offer it in three levels.
How Does Schellman's Ransomware Preparedness Assessment Work?
You’ll need to consider a few factors first to understand what tier you need. Internally, assess the following:
- Your business unit risks
- Your appetite for better data points (i.e., validation of responses)
- Your resource accessibility (i.e., personnel availability)
Knowing that, you may choose to mix and match the level of effort you want to undertake per business unit or operating segment. In any case, here are the various tiers—and their matching investment needs—for your consideration:
|
Type |
Nature |
Your Level of Effort |
|---|---|---|
|
Tier 1 |
|
Low:
|
|
Tier 2 |
|
Moderate:
|
|
Tier 3 |
|
Moderate/High:
|
*Highly dependent on the sophistication of evidence gathering techniques, experience, and level of executive leadership sponsorship.
How to Further Prepare Against Ransomware
Once you’ve gone through this assessment and understand your current position, you’re going to want to know what to do next.
We’ve got you covered there as well.
Below we’ve laid out a roadmap demonstrating different routes you could take to improve your ransomware preparedness and overall cybersecurity posture.
Within this roadmap, there are three stages:
- Discovery Stage: Understand your current cybersecurity posture.
- Validation Stage: Have a third-party provide validation of your cybersecurity posture and assess those data points you collect.
- Differentiate Stage: Leverage that validated understanding to gain more specific technical insights and position yourself with a more competitively advantageous cybersecurity posture that provides value to your organization, customers, and business partners.
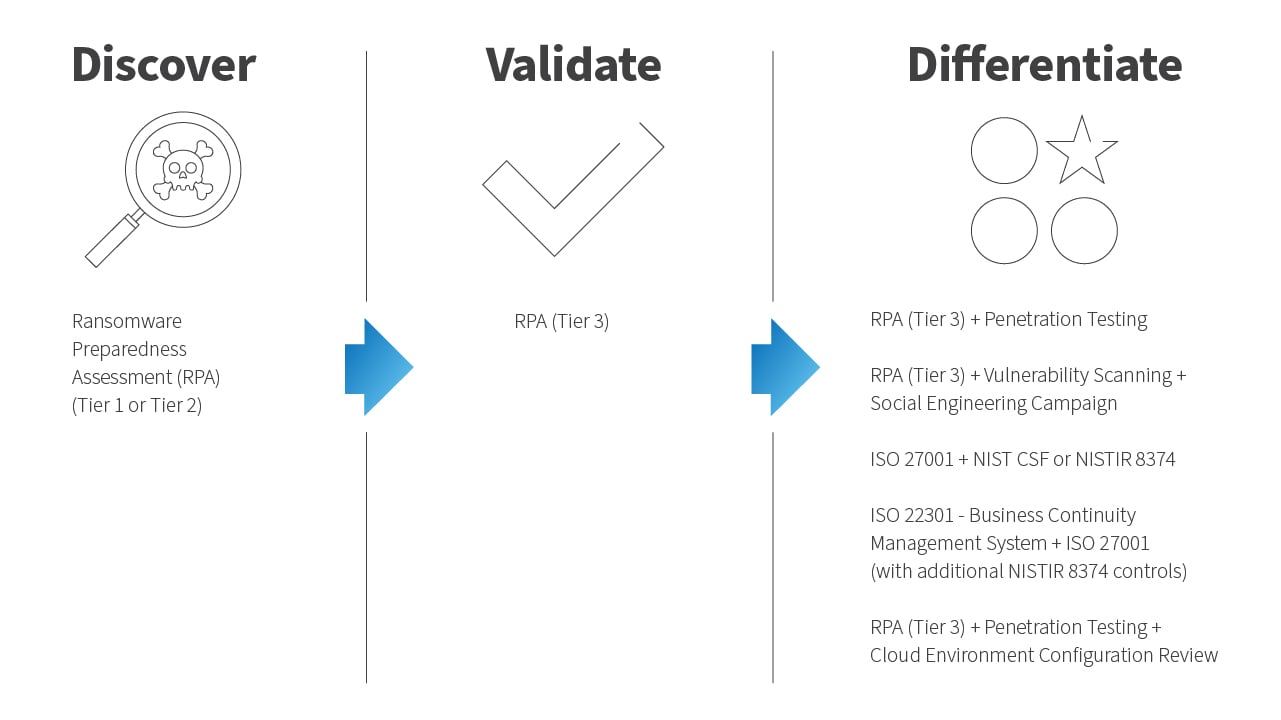
The last phase is where all your options really diversify, but if you follow this process after having assessed your current ransomware preparedness, you’ll be ready to move forward towards either a compliance initiative or a more sophisticated cybersecurity posture.
Not only can each of those different assessment options help you both sleep better at night, knowing your cybersecurity measures have been independently evaluated, but each can also demonstrate to your customers—and prospective customers—that you are serious about protecting their information against ransomware and other attacks.
Next Steps for Your Cybersecurity
Given his aforementioned quote, Stewart Brand would probably agree that technology can be a double-edged sword—the advancements serve to progress society forward, but they can also open doors for malicious attackers to take advantage of you and other organizations.
But now you know there’s a way to determine where you stand. Not only do you understand ransomware as a concept, but you now have the option of a Ransomware Preparedness Assessment. Taking into account the specific elements of your organization, this evaluation can provide you with a better grasp of your cybersecurity posture and open up options to improve it.
As you consider your way forward, make sure to also read our further content on related subjects. The articles below provide details on specific protections, methods, and validations—one of which we already mentioned in ISO 27001—that can help you stay safe from ransomware and other cyber threats:
- Are You Ready for Ransomware?
- 5 Cornerstones to a Successful Cybersecurity Program
- 10 Steps to Help You Prepare For ISO 27001 Certification
We’re also hosting a public webinar on Friday, April 1st at 1 p.m. EST that will touch on these subjects. Together with our partners at Sheltered Harbor, we’ll be discussing cyber resilience, including preparation for cyber threats like ransomware and other current possibilities. We’ll also build on what we’ve said here regarding Ransomware Readiness considerations, with more detail on how this assessment can help you prevent and prepare. To register for this webinar, click here.
But if you find that you have specific questions regarding the Ransomware Preparedness Assessment, other cybersecurity measures, or how your organization can leverage compliance into a competitive advantage, please also feel free to contact us directly. We’re happy to set up a conversation to discuss how you can best protect yourself—and how we can help you do that.
About Bryan Harper
Bryan Harper is a Director with Schellman. Prior to joining Schellman in 2017, Bryan worked as a Senior IT Auditor, specializing in SOC examinations. Bryan also worked as a staff accountant in a public accounting firm performing financial audits, consulting, and out-sourced internal audit engagements for clients in the banking, insurance, and healthcare industries. Bryan is now focused primarily on SOC examinations for organizations across various industries. At Schellman, Bryan is involved with technical training development specific to auditing cloud services and supports Schellman's cybersecurity task force, which is responsible for monitoring developments in and responding to cybersecurity regulations and related cybersecurity compliance frameworks.




