
Every year, the online gaming industry generates billions of dollars in revenue, thanks to millions of players worldwide. In fact, more likely than not, someone in your own life spends time playing games online—games like Fortnite, League of Legends, and CounterStrike, which have all cultivated large followings and are now household names.
The ideas of competing, moving up through the ranks, and improving skill make these games attractive to a diverse audience, especially when playing well often leads to added perks such as exclusive in-game rewards. A small percentage of highly skilled players even make money via live streaming gameplay on Twitch or by creating YouTube highlight reels. Unfortunately, the inclusion of such potential, even monetary benefits has now forced some players to resort to unethical means of winning.
[Cheating? Inconceivable!]
Yes, cheating is a prevalent issue in this space. Irdeto, a digital platform security company in the entertainment and video game industries, conducted a survey in 2018 that revealed approximately 60% of online gamers have had their experience negatively impacted by other players cheating, while 77% are likely to stop playing if they believe others are cheating—moreover, of those surveyed, 37% actually did admit to cheating in some capacity, and such numbers paint the true picture and scale of cheating in online gaming. Though people cheat mostly for prestige and occasionally for money, some of them do not realize that their actions in the digital world also have real-life consequences, as honest players may end up restricting play to their close friends or cease playing altogether. Even still, cheating remains rampant—but how is it done?
One tactic used by cheaters is through software modification where underlying system components are altered to gain competitive advantage. For example, by exploiting bugs or modifying certain drivers, gamers can see enemies through walls or remove obstructive elements from the game completely—an appropriately dubbed “wall hack.” Another popular cheating method is using an aimbot, which allows for perfect aim or target acquisition—a helpful hack in multi-player, first-person shooter games. Both methods are relatively simple techniques, but they grant cheaters sizable benefits at others’ expense, and as trustworthy players are driven away in frustration, video game development companies stand to lose millions in revenue. What can they do to stop corrupt gameplay? One solution is the implementation of anti-cheat software to help curb these kinds of in-game modifications.
[Anti-Cheat: To Kernel and Beyond!]
Commonly, anti-cheat software initiates a signature-based scanner to detect possible cheats and vulnerabilities within a computer’s memory and processes. If the scan detects any anomalies, an incident report is sent to the gaming company’s engineers for analysis, where a match between the cheat and the engineers’ database will lead them to flag the account, whereas any new cheats discovered will be added for future investigations.
Anti-cheat software has long worked in user-mode, also known as Ring 3. At this level, the software cannot directly access underlying hardware or reference memory, so permission must be obtained from the system application programming interface (API) before any scanning occurs. Moreover, applications run in isolation while in user-mode and therefore cannot alter data that belongs to another application. As such, while anti-cheat software running in user-mode can conduct signature scanning, a fault in the driver will silo any potential damage.
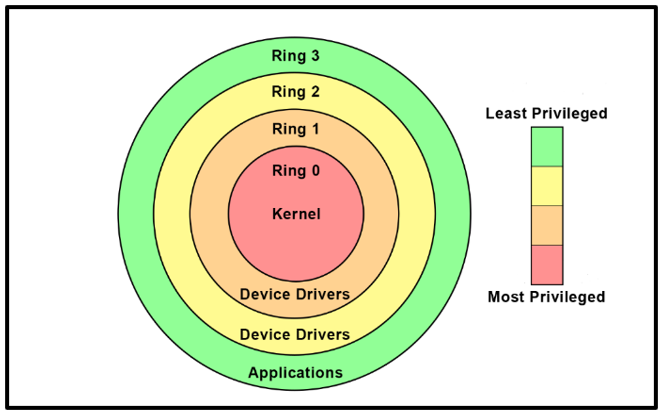
Knowing this, cheat developers have created more sophisticated methods to circumvent Ring 3 anti-cheat software. They have begun running cheats at higher privileges, namely at the kernel level or Ring 0. Software at this level does not have the restrictions of Ring 3 and can execute any instructions and reference any memory address. In kernel-mode, cheats can even hook system calls that anti-cheat software running at level 3 relies on to retrieve data. As a result, the software detects modified results, believes the data to be legitimate, and does not flag the account, rendering itself moot.
But the battle isn’t over, as companies have also upped their game and established anti-cheat software that requires the download of a kernel-mode driver. Anti-cheat software running at Ring 0 can monitor the system for data integrity that the same thing at Ring 3 would have been scanning, but now, the scanning occurs “at the source,” making it significantly harder to create undetectable cheats.
In fact, companies such as Epic Games and Battleye are already utilizing some form of these kernel-mode drivers for their anti-cheat software, and Riot Games is the latest company to make this update. As their rationale for their switch, they conceded that, until now, they had “been forced to play this game from the user-level, effectively giving cheaters a much-needed, twelve stroke handicap” in a recent message to customers—this is a disadvantage that the protection of a kernel driver will eliminate. Like Riot, game developers are doing everything in their power to stay ahead of novel cheating strategies so they can provide the best gaming experience for their customers, keeping them coming back for more, and the kernel-mode driver does allow for more effective detection of cheats.
[Show Me the Security]
While these companies may have the best intentions when it comes to protecting the integrity of their games, regrettably, the increased efficacy comes at a cost to player security and privacy. Problems with anti-cheat software may result in system-wide instability, as well as offer hackers a potential new avenue into players’ computers. According to an article by ArsTechnica, any flaws in an anti-cheat software’s driver code at the kernel level could result in “blue screen of death”-style crashes, while serious oversights in the code could allow a buffer overflow exploit. In fact, hackers might even gain complete access to machines with a successful kernel attack, subsequently penetrating the player’s network and router through either the Wi-Fi or Ethernet connection, thereby exposing all connected devices on the network to unauthorized access and misuse. This is an enormous problem under normal circumstances, but considering how most of the world is currently under lockdown with many employees working from home, a gaming station on the same network as a work asset means the potential reach of the attack could be even more catastrophic. Though these kinds of disastrous scenarios may seem hypothetical or distant, it should be emphasized that existing kernel-level anti-cheat functions probably already have some insecurities.
Given all of this, if companies are going to require such low-level access to machines, then they also have an obligation to their consumers to uphold safety measures for personal data. Depending on where the companies themselves are located, they may already have a legal duty to fulfill that state or country’s privacy requirements, but gaming organizations can provide consumers further comfort regarding their practices through third-party assurances such as cybersecurity or privacy assessments. Recommended avenues include penetration testing and social engineering testing, as these security-related third-party assessments generally test for data protection measures in three major areas:
-
Administrative
Security governance/program definition, employee training, and vendor oversight -
Technical
Access controls, encryption, and security measures for computer systems -
Physical
Facilities, environmental safeguards, and business continuity and disaster recovery
These processes, among others, are crucial to ensure data protection for consumers, who need to trust that companies can not only can protect their data, but can also react quickly to patch vulnerabilities if things become compromised, including anti-cheat drivers—as the Ring 3 and Ring 0 software also permit gaming companies some surveillance capabilities, an administrative measure like data classification becomes even more essential. Though cheating remains an important issue that is necessary to curb, data breaches are an even more repercussive danger looming in the shadows of the gaming industries and, as such, companies must work to find a balance between preventing cheating and ensuring security and data protection for their consumers.



