Which of the NIST SP 800-Series Publications Should You Follow?
Published: Feb 23, 2022
Last Updated: Oct 19, 2023
When it comes to IKEA, we’d all probably agree that the Swedes make some great flat pack furniture that can either upgrade your space or just do in a pinch.
But for all the opportunity they provide, buying from IKEA means dealing with what have become their famous assembly instructions. They might be meant to guide you, but oftentimes it’s easier to lug those boxes from the car to their spot in your house than it is to make sense of the directions they give you to build your purchase.
The situation can be very similar when it comes to publications from the National Institute of Standards and Technology (NIST).
As part of its core functions, NIST provides cybersecurity frameworks that are a line item for most government contracts, but are also widely accepted as a solid launch point for cybersecurity efforts.
But while they may be meant to help you, deciphering what these publications actually mean and if they even apply to your organization can be as difficult as following IKEA bookcase assembly instructions.
You may be on your own when it comes to budget Swedish furniture, but in this article, we’re going to simplify the intentions of three of the more popular NIST publications.
Schellman has been operating in the federal compliance space for years as an accredited FedRAMP 3PAO (and now CMMC C3PAO), and we have walked the NIST path with clients plenty of times before. In this article, we’ll leverage that significant experience and speak plainly about NIST 800-37, 800-53, and 800-171.
After you understand what each’s purpose is and how they can help you, you’ll be able to make a more informed decision on which publications are best associated with your organization’s compliance efforts.
What is NIST 800-37?
We start here, because among all the other possibilities, NIST 800-37 can help you establish what it is you want to accomplish with your cybersecurity. Of all the others we’ll discuss, this publication is the most like those IKEA instructions, because you can also consider it as building guidelines—it’s just you’re building out your security and privacy controls, not a DIY coffee table.
How does NIST 800-37 help you do that? It provides what they call Risk Management Framework that is designed to help organizations get into the headspace necessary to provide cybersecurity—particularly security that holds up against federal standards.
Within the world of compliance, there are many different approaches to stacking your cybersecurity controls—you could go the way of SOC, or even ISO 27001. The contents of NIST 800-37 provide a different way, using the cycle below:
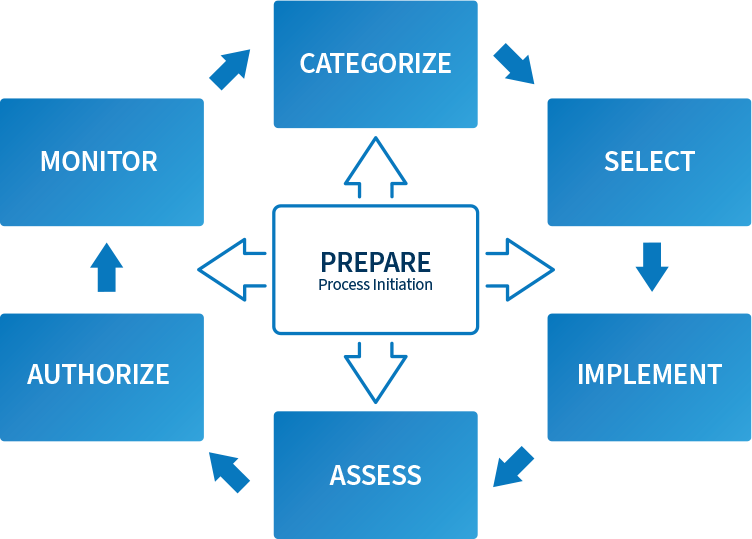 The process breaks down as follows:
The process breaks down as follows:
- Categorization: 800-37 provides guidance that can strengthen your understanding of your system. As you document its characteristics, you’ll divide your data into risk classes depending on its potential adverse impact.
- Selection: After you understand what data you’re handling and how much risk it poses to you, you’ll be better positioned to select your controls. As it is just meant as initial guidance, 800-37 does not provide any standard list of controls itself. Rather, you can choose from different baselines—including that of 800-53 (which we will get into later)—before adding others depending on the kind of information passing through your system.
- Implement, Assess, Authorize, Monitor: Once your controls are selected and you do the work to implement them, you can be formally assessed. Although there is no assessment directly associated with NIST 800-37, your work establishing this foundation can be evaluated against other related standards like FISMA (among others). A successful assessment—whichever you eventually choose—leads to authorization, and then your system is routinely monitored as time passes.
Following the above security lifecycle laid out by NIST 800-37 can go a long way towards establishing solid security practices. For those organizations looking to implement a consistent risk management process that can facilitate a mature security and privacy program for their information system, NIST 800-37 can help.
Not only does this publication provides guidance on security and privacy controls for your entire organization from the top down, but it can also help prepare your organization for other, future assessments.
What is NIST 800-53?
If NIST 800-37 offers a way to go about constructing your security baseline, then NIST 800-53 is an actual regulatory standard. The publication actually contains the recommended minimal control guidance for federal information systems—actual requirements you can meet—and offers them as a controls catalog.
What’s more is, this control guidance is basically the cybersecurity compliance backbone for all federal systems. Whether you support an on-premises system that needs to be FISMA compliant, or you’re in the cloud looking at becoming FedRAMP authorized, you should concern yourself with 800-53 because you’re going to run into these control basics:
- NIST 800-53 provides groupings of operational, technical, and management controls that can strengthen your security and privacy.
- NIST 800-53 provides three control baselines, each with a minimum number of security controls needed to mitigate the level of risk. These 3 levels of risk are low, moderate, or high, and the baselines for each are based off security impact of a system.
- The controls are organized into security control families, tackling topics like access control and personnel security. The selected controls will be tailored according to your system’s categorized baseline of low, moderate, or high. As it is a standard of its own, you can be evaluated against NIST 800-53, and the results can be beneficial, especially when attempting to bridge to your desired federal standards like FISMA or FedRAMP.
But no matter what you do, if you're in the federal compliance space, you'll likely come across this special publication in its raw form, tailored, or leveraging another publication that has derived it's controls from 800-53.
And even if you don’t, NIST 800-53 is widely accepted within the greater commercial industry as a strong cybersecurity compliance control set; therefore, it can benefit you to implement its controls and be evaluated against it.
What is NIST 800-171?
Now, if NIST 800-53 provides a baseline of security and privacy controls, then this last publication represents an add-on to that backbone. More specifically, NIST 800-171 shines the spotlight on controlled unclassified information (CUI).
How to know if your system hosts CUI?
If you’re working with an agency already, their program management office can offer you specific guidance. But for a general sense, details can be found on the CUI Registry. As far as publication 800-171 relates, it provides security requirements that apply to nonfederal systems that process, store, transmit, or secure this CUI.
In this case, “nonfederal systems” translates to those provided by government contractors (primes and subs)—if you’re already doing business with the government that involves CUI, chances you’ve probably been asked to get assessed against this control set or to at least self-attest to meeting it. If you’re trying to win this kind of work, you will be expected to have the security requirements outlined in NIST 800-171 in place.
The controls actually are a subset of NIST 800-53—they address a number of things like access control, physical security, and coding practices. The idea is that if you build a system meant to host this kind of sensitive government information, you must secure it like the federal government does it themselves—e.g., what is stipulated in NIST 800-171.
But perhaps the most critical point regarding 800-171 is its relation to the Cybersecurity Maturity Model Certification (CMMC). A new framework aimed at securing this kind of information among defense contractors, CMMC actually builds on the 800-171 requirements—if that path is looking likely for your organization, you should go ahead and take a look at these controls.
Choosing the Right NIST Direction
Discerning the bottom line from all the various NIST 800 series publications can be a bit like decrypting IKEA’s oft-confusing furniture assembly instructions. There are so many different things out there, it can be difficult to know the right next step.
You may still have to fumble around with furniture parts from Sweden after your next IKEA purchase, but that won’t be the case when you make your decision on useful NIST publications. Now, you know a little more about three of the more relevant publications that NIST has put out, which should help in pointing your compliance compass towards a clear next step.
While NIST 800-37 can provide you with a solid, all-encompassing approach when it comes to risk management—no matter if you have intentions to do business with the federal government or not—publications like 800-53 and 800-171 provide actual security controls that may or may not apply to you.
Where you proceed from here will be determined by which is more suited to your needs, your intentions, and what kind of data your system currently handles or will handle in the future. If you’d like to speak more about federal assessments and how best to stack your compliance, please reach out to us—we’re happy to have a conversation that will simplify federal compliance even further for you.
About the Authors:

Doug Stonier is a Manager at Schellman based in Knoxville, Tennessee. Doug has over 8 years of experience with focus in the Government & Public Sector focused primarily on FedRAMP assessments for cloud service providers.
 Tim Walsh is a Manager with Schellman based in Massachusetts. Prior to joining Schellman in 2019, Tim worked as a Systems Engineer for a Defense Contractor specializing in the design of physical security systems for Naval installations across the United States. Tim is now focused primarily on managing FedRAMP engagements as part of a Third Party Assessment Organization for Cloud Service Providers seeking FedRAMP Authorization.
Tim Walsh is a Manager with Schellman based in Massachusetts. Prior to joining Schellman in 2019, Tim worked as a Systems Engineer for a Defense Contractor specializing in the design of physical security systems for Naval installations across the United States. Tim is now focused primarily on managing FedRAMP engagements as part of a Third Party Assessment Organization for Cloud Service Providers seeking FedRAMP Authorization.
About Schellman
Schellman is a leading provider of attestation and compliance services. We are the only company in the world that is a CPA firm, a globally licensed PCI Qualified Security Assessor, an ISO Certification Body, HITRUST CSF Assessor, a FedRAMP 3PAO, and most recently, an APEC Accountability Agent. Renowned for expertise tempered by practical experience, Schellman's professionals provide superior client service balanced by steadfast independence. Our approach builds successful, long-term relationships and allows our clients to achieve multiple compliance objectives through a single third-party assessor.



