Prepare for CMMC: Three Things You Can Do Right Now
Published: Jun 7, 2022
Last Updated: Feb 18, 2025
If you’ve never seen Man vs. Wild, it’s a television show featuring famed adventurer Bear Grylls who, in every episode, is stranded in mostly wild terrains with his film crew. His task is to get back to civilization successfully, and he showcases different survival skills during those journeys.
If you were to ask Bear, who also runs a survival academy, he’d probably stress that success boils down to preparation when faced with the unknown.
You could consider that true for most compliance projects as well, but especially where it concerns the unknown terrain that is CMMC.
The Cybersecurity Maturity Model Certification (CMMC) is creating quite the buzz within the Defense Industrial Base, particularly following the Department of Defense (DoD)’s November 2021 release of the CMMC 2.0 model overview, assessment guides, and scoping documents.
These changes are expected to be reflected in the Pentagon’s final rulemaking process and subsequent changes to the Code of Federal Regulations (CFR) and Defense Federal Acquisition Regulations Supplement (DFARS), but final rulemaking remains some months away.
As one of the first CMMC C3PAOs authorized to perform these assessment services when the certification finally goes live, we understand that interested organizations may be waiting with bated breath until the official launch—we are too.
So that you’re as successful as possible when that time does come, we recommend the Bear Grylls mindset—failing to plan is the same as planning to fail, and we’re going to help you avoid that failure.
What actions can you take today regarding CMMC? Here are three recommendations to help prepare to the utmost.
How to Prepare for CMMC
1. Leverage Existing Requirements.
CMMC v2.0 may seem like a “brand new” standard for cybersecurity across the defense industrial base, but it’s actually not.
In fact, the sources for these compliance requirements already exist in some form today. For example:
- Executive Order 13800 “Improving the Nation's Cybersecurity:” Implements bold measures for the prevention, detection, assessment, and remediation of cyber incidents.
- Executive Order 14028 “Improving the Nation’s Cybersecurity:” Charges multiple agencies—including NIST—with enhancing cybersecurity through a variety of unique initiatives intended to further fortify the security of federal systems and data.
- Federal Acquisition Regulations (FAR) 52.204-21: Requires the “basic safeguarding of contractor information systems that process, store, or transmit Federal contract information.” It imposes fifteen (15) basic cybersecurity controls for “covered contractor information systems” by which “Federal contract information” (FCI) is received, stored, processed, or transmitted.”
These controls are intended to function collaboratively and require that contractors:
- Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
- Verify and control connections to and use of external systems.
- Control information posted or processed on publicly accessible systems.
- Identify information system users, processes acting on behalf of users, or devices.
- Authenticate (or verify) the identities of those users, processes, or devices, as a prerequisite to allowing access to organizational systems.
- Sanitize or destroy system media containing Federal Contract Information before disposal or release for reuse.
- Limit physical access to organizational systems, equipment, and the respective operating environments to authorized individuals.
- Escort visitors and monitor visitor activity, maintain audit logs of physical access, and control and manage physical access devices.
- Monitor, control, and protect organizational communications (e., information transmitted or received by organizational systems) at the external boundaries and key internal boundaries of the systems.
- Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
- Identify, report, and correct information and system flaws promptly.
- Protect against malicious code at appropriate locations within organizational systems.
- Update malicious code protection mechanisms when new releases are available.
- Perform periodic scans of the system and real-time scans of files from external sources as files are downloaded, opened, or executed.
- Defense Federal Acquisition Regulations Supplement (DFARS) 252.204-7012 extends these requirements by ensuring you provide “adequate security” for covered defense information (CDI) that is processed, stored, or transmitted on your internal information systems or networks.
- As part of these protections, you’re required to implement the National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 “Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organization” which mandates 110 individual cybersecurity controls for implementation and maintenance, including the development of a System Security Plan (SSP) and compliance with cyber incident reporting requirements.
- For Cloud Computing environments, DFARS 252.239-7010, “Cloud Computing Services” will also apply.
- Stipulates that you “shall implement and maintain administrative, technical, and physical safeguards and controls with the security level and services required in accordance with the Cloud Computing Security Requirements Guide (SRG), unless notified by the Contracting Officer that this requirement has been waived by the DoD Chief Information Officer.”
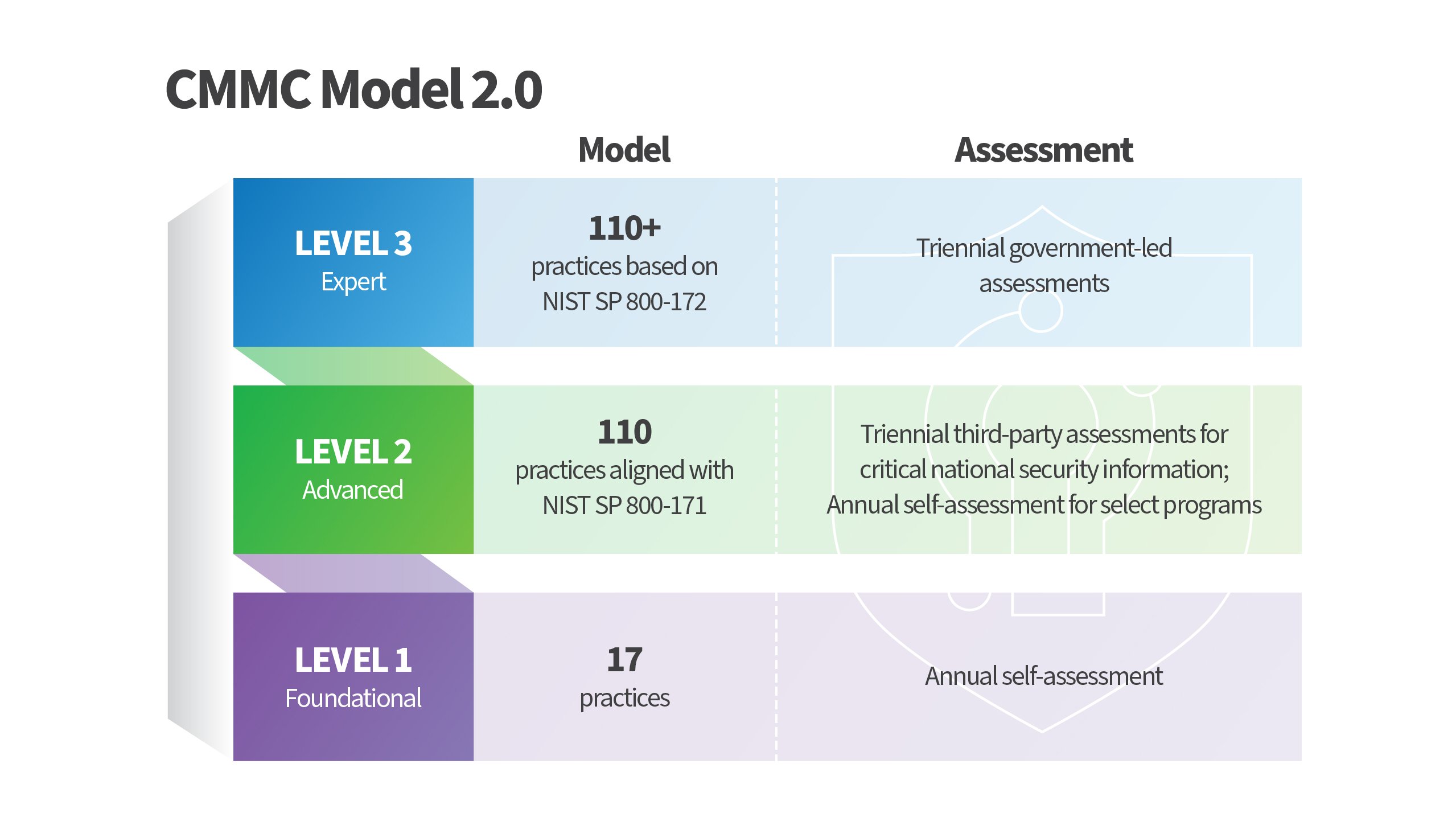
Drawing from elements of these already published regulations, the CMMC will provide a unifying framework by which your cybersecurity resiliency may be objectively measured and independently verified. The model will be organized into three cybersecurity levels—Foundational, Advanced, and Expert—and largely aligned to the NIST SP 800-171 standard.
Each of these levels comprises a unique set of CMMC practices and correlating assessment requirements:
- Level 1 (Foundational): Encompasses the basic safeguarding requirements for FCI specified in FAR Clause 52.204-21.
- Level 2 (Advanced): Encompasses the security requirements for CUI specified in NIST SP 800-171 Rev 2 per DFARS Clause 252.204-7012 [3, 4, 5].
- Level 3 (Expert): Will contain a subset of the security requirements specified in NIST SP 800-172.
Based on all this, you have the resources to begin your CMMC efforts today, despite a lack of formal publication. We encourage you to use them to get started in identifying the sources and nature of data you’re contractually bound to protect, including:
- The authority by which this data is shared;
- The mechanisms for protection (in transit and at rest);
- The shared responsibilities, if applicable; and
- Their obligations under the relevant legislative guidance.
2. Take Advantage of Outside Resources.
As you prepare, we also recommend you engage qualified expertise sooner rather than later, and the CMMC Accreditation Body (CMMC-AB) has made it easier for you to find it.
In coordination with the DoD, they’ve established a CMMC Marketplace that provides a searchable listing of pre-vetted, credentialed organizations and individuals who are available to support your compliance needs. Each member of the CMMC Marketplace has received specialized training—including governance and regulatory training—and is bound by a very strict Code of Professional Conduct.
Having that expertise alongside you could prove incredibly beneficial. Did you know, that just because a requirement isn’t specifically delineated in the terms of your government contract, that doesn’t make it not applicable?
The decision in G. L. Christian and Associates v. the United States—otherwise known as Christian Doctrine—requires that even if a mandated clause is omitted, the contract must be interpreted as if it contains the omitted clause. If your contractual terms are inconsistent with current statutes and regulations—e.g., requiring less than is presently mandated—the courts must interpret that the contract be read as if it contained the omitted requirements.
That could potentially complicate things for you—there’s greater potential for compliance violations, and legal repercussions due to misunderstanding or misinterpretation of these compliance requirements—so it would be wise to leverage the expertise that has been curated for you in the CMMC Marketplace.
3. Kickstart the Necessary Human Investment.
Successful compliance is contingent upon a variety of factors, including governance and sustainment of the implemented controls. Cybersecurity isn’t relegated to a subset of the organization anymore—it’s become everyone’s responsibility,” and that may represent a paradigm shift for some organizations.
Now more than ever before, “human firewalls”—employees at all levels throughout your organization—are the primary, and often most effective, defense against cyberattacks. Getting them up to standard is not going to happen overnight, and it won’t be easy.
Train your personnel to only understand the nature and impacts of a cyberattack, but to also recognize and report indicators of potential threats. As threats evolve, so must your internal capabilities and competencies.
Getting Ready for CMMC
Given the high stakes of CMMC compliance, it’s best that you start now with the Bear Grylls approach—prepare, and prepare well. By following through with the three tips we detailed, you’ll be in that much better of a position when CMMC is finally launched.
For more breakdowns and information regarding this new framework, check out our other articles:
- Cybersecurity and the Federal Government
- CMMC 2.0 Scoping Insight: 2 Tips For Using PCI Context to Understand Your Potential Scope
We can also save you a look-through of the CMMC Marketplace if you need more specific expertise. Reach out to us, and we can set up a conversation with our CMMC Certified staff to address any questions you may have.
As you do that though, keep in mind that Schellman is a CMMC Third-Party Assessment Organization (C3PAO)—that’s very different than a Registered Provider Organization (RPO).
The latter can assist with CMMC preparation and implementation, whereas C3PAOs—i.e., Schellman—only perform CMMC assessment services. If you do need CMMC advisory, preparation, and implementation services, you’ll want to work with a reputable advisory organization or RPO before you engage Schellman when you’re ready for an assessment.
About Schellman
Schellman is a leading provider of attestation and compliance services. We are the only company in the world that is a CPA firm, a globally licensed PCI Qualified Security Assessor, an ISO Certification Body, HITRUST CSF Assessor, a FedRAMP 3PAO, and most recently, an APEC Accountability Agent. Renowned for expertise tempered by practical experience, Schellman's professionals provide superior client service balanced by steadfast independence. Our approach builds successful, long-term relationships and allows our clients to achieve multiple compliance objectives through a single third-party assessor.



