Do I Need a PIN Assessment?
Published: Nov 30, 2021
Last Updated: Oct 19, 2023
If you’ve been around since the mid-1970s, chances are you’ve made use of a debit card at a time or two.
And if you’ve partaken in that, you’ve chosen a Personal Identification Number (PIN) as well, for use while shopping or at an ATM.
That’s how most people regard PIN, as a verification method for some transactions.
But did you know that in fact, PINs are also used by organizations to verify consumers and their use of credit cards in order to reduce fraud?
It’s there in the name—a PIN is a personal identification number, and the compliance space exists to protect delicate information like this. As one can imagine, the loss of integrity for PIN data can have serious consequences for the acquiring bank, merchant, and cardholder alike.
And so, among the sea of different certifications, examinations, and assessments that exist to validate security measures regarding data of this nature, the PIN gets its very own evaluation.
In this article, we’ll delve deeper. We’re going to pinpoint exactly what types of organizations could use a specific assessment of this nature. We’re also going to provide a high-level breakdown of the data interchanges that are relevant to this kind of review. Afterwards, you’ll have a better grasp on if this assessment would benefit you, as well as an understanding of what would be evaluated.
This will put you in a better position to tailor your compliance needs accordingly, so let’s jump in.
What Occurs During a PIN Transaction?
To better understand what is reviewed during a PIN assessment, we can deconstruct a basic transaction, as seen below:
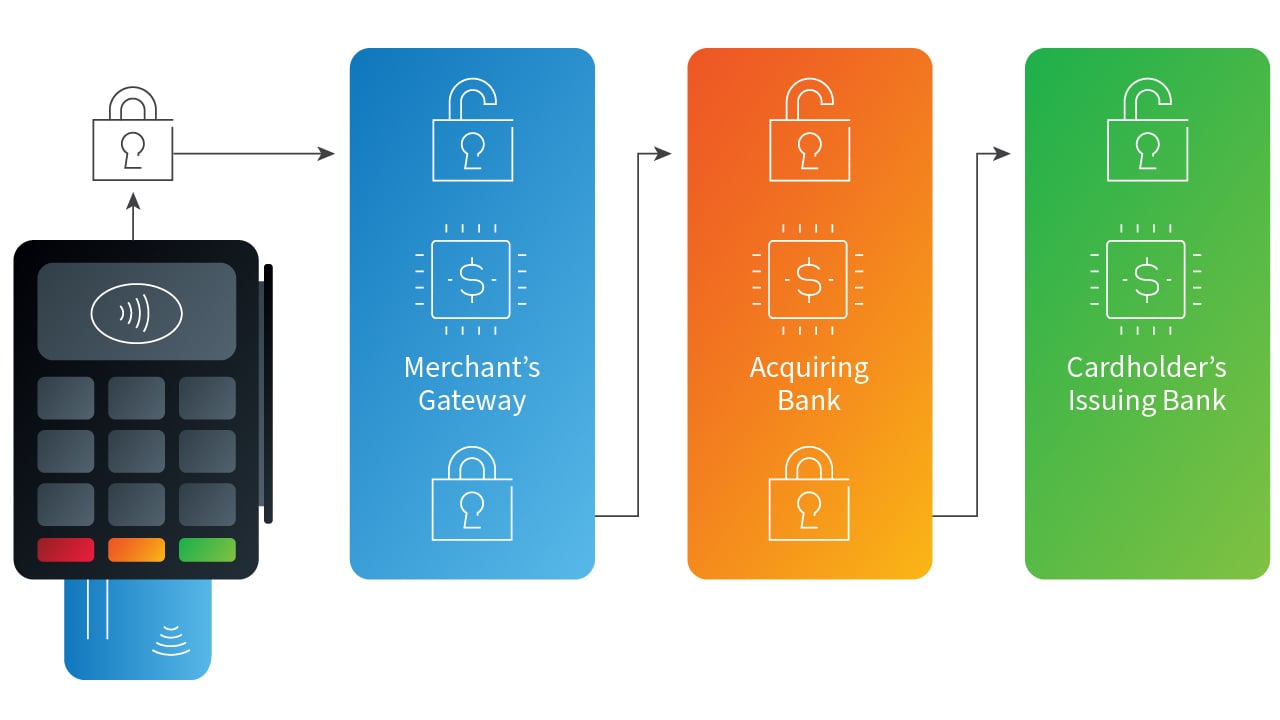
This diagram demonstrates the basic exchange of PIN data from a high level. Let’s spell it out, from left to right:
- When making a transaction, the cardholder uses the terminal to swipe, dip, or tap their card and, when prompted, enters their PIN.
- The card reader will encrypt the PIN data using a unique key and send that, along with the credit card number, to the merchant’s gateway.
- The merchant gateway identifies the terminal to recreate the key, decrypts the PIN and encrypts it with the acquirer’s working key before transmitting to the acquirer.
- The acquiring bank will decrypt the PIN value using their working key and using the first six digits of the card number (BIN) will identify the corresponding issuer’s working key, encrypt the PIN and transmit to the issuer.
- The issuer will decrypt the PIN with their key and compare the number with the PIN previously set by the cardholder. If the values match, then the transaction is authorized and a response is sent to the terminal.
(This is a simplified example, but it demonstrates one of the many ways that PIN data flows within and across financial institutions through its use as verification.)
The point is, a large number of organizations support this process. If your organization is somehow managing, processing, or transmitting PIN data during online and offline payment card transactions, a PIN assessment will evaluate your encryption and key management of PIN transactions as relevant, as well as the secure management of any relevant processing equipment.
Who Needs to Undergo a PIN Assessment?
As can be the case for many compliance standards, the need for this assessment is almost always driven by outside factors—regarding PIN, these can be things like customer requirements, an acquiring bank, business relationships, or your participation in payment brand networks.
The majority of these assessments have applied to payment gateways and acquiring banks that maintain a Hardware Security Module (HSM) for the encryption and decryption of PIN data.
But it’s not just them.
To make it all simpler, you may need a PIN assessment if you are an organization that does one or more of the following:
- Receives PIN data from merchants
- Stores, processes, or transmits PINs on behalf of your clients
- Performs key injection directly or remotely for your own devices or those of your customers
- Services, supports, or deploys devices that process and accept PIN data
- Provides certification and registration authority services
- Performs PIN translation
- Performs key management services
- Manages terminals that accept PIN
What are the Requirements of a PIN Assessment?
Alright, you think you may qualify. But it’s likely that there is still some apprehension about a new kind of assessment that remains, so if you tentatively wish to move forward, let’s identify what you will be stacked up against during this evaluation.
Going in, the scope of your PIN assessment will be commensurate with your relevant services supported, and it will be evaluated against a set of seven designated control objectives during your assessment.
In detail, these seven objectives are:
- Control Objective 1: PINs used in transactions governed by these requirements are processed using equipment and methodologies that ensure they are kept secure.
- Control Objective 2: Cryptographic keys used for PIN encryption/decryption and related key management are created using processes that ensure that it is not possible to predict any key or determine that certain keys are more probable than other keys.
- Control Objective 3: Keys are conveyed or transmitted in a secure manner.
- Control Objective 4: Key-loading to HSMs and POI PIN-acceptance devices is handled in a secure manner.
- Control Objective 5: Keys are used in a manner that prevents or detects their unauthorized usage.
- Control Objective 6: Keys are administered in a secure manner.
- Control Objective 7: Equipment used to process PINs and keys is managed in a secure manner.
These control objectives are comprised of 33 individual security requirements that your technologies, personnel, and documentation must meet. A high-level breakout of what these include are:
- For technologies, this includes a review of your equipment to demonstrate that it is:
- Physically secured and protected against unauthorized access;
- Configured to securely manage and exchange data;
- Accessible only by staff with a business need; and
- Generating logs that can trigger alerts based on content.
- Regarding your personnel, interviews are conducted with the personnel performing tasks relevant to PIN—these conversations often act as the dovetail between documentation and observations.
-
The review of documentation encompasses:
- Both your policies and procedures for handling PIN data;
- Key management processes;
- Key conveyance with other organizations; and
- Steps taken by staff if a compromise or error is detected.
Because your scope is limited to just the relevant services provided, any requirements that do not apply to your organization will be marked as “not applicable” along with the justification as to why.
We should also note that the PIN standard also includes Annexes A1, A2, and B in addition to these seven objectives. And while each Annex includes the same seven control objectives in format, these specifically only apply to organizations that perform remote key distribution using asymmetric techniques, certification and registration authority operations, or maintain a key-injection facility.
If that last sentence just made your brow furrow, you are not alone. Like other security standards, PIN security is complex, and it can sometimes feel like the journey goes from zero to sixty pretty fast.
Next Steps
But don’t worry. In speaking with an assessor directly, a lot of the questions you may have regarding how this assessment will work for you can be answered.
For Schellman’s part, our staff have performed readiness assessments on PIN for dozens of organizations and completed assessments on each subset of the standard—we can attest that the experience has provided us with lots of insight, not only regarding the actual conducting of the assessment but also in providing guidance where requirements are not met. Should you have any questions right now, we are happy to set up a call in order to deconstruct more of the particulars surrounding this kind of security.
But if you’re not yet ready to commit to a conversation, that’s no problem too. If you’d prefer to continue foraging around for more information regarding PIN assessments, watch this space for more information from Schellman in the coming weeks.
About Sully Perella
Sully Perella is a Senior Manager at Schellman who leads the PIN and P2PE service lines. His focus also includes the Software Security Framework and 3-Domain Secure services. Having previously served as a networking, switching, computer systems, and cryptological operations technician in the Air Force, Sully now maintains multiple certifications within the payments space. Active within the payments community, he helps draft new payments standards and speaks globally on payment security.




