How to Read Your Vendor's SOC Report
Published: Mar 11, 2022
Last Updated: Jan 19, 2024
One of the most famous lines from the Spider-Man mythos goes like this: “With great power comes great responsibility.”
The character who coins that phrase (Uncle Ben) doesn’t actually have powers like his nephew, Peter Parker, so nor does he carry the weight of that responsibility. But when it comes to compliance, you actually have both.
Your responsibility is more obvious—you bear the burden of providing assurance to your customers that the data and services they entrust with you is safe. But you also have power in compliance—more specifically, the power to demand compliance from your vendors.
Going forward, we’ll define the term “vendor” as any third party that provides you with a good or service relevant to your control environment. That could include colocation services, data management services, security services, or hardware and software products, among others.
But the point is, if you’re beholden to SOC standards by your customers, as a customer yourself, you also have certain power to ask the same of these third parties that, in turn, provide services to you.
But how should you go about that? Which SOC report should you ask for from these vendors? And how should you interpret the reports you do get?
In this article, we will detail the answers to all these questions. SOC is a foundational service for Schellman—we have over two decades of experience with this brand. Now, we want to help you wield this power you have for your maximum benefit.
Once you’ve read through this information, you’ll have a better idea of what SOC report to ask for and where to look for the important information you need once that report is in your hands.
What Kind of SOC Report Should You Request From Your Vendor?
There are currently five (5) brands of SOC reports, all of which can provide you or your vendor with different assurances:
|
Intended to provide assurance relevant to the internal control over financial reporting. |
|
|
Intended to provide assurance relevant to the security, confidentiality, availability, processing integrity, or privacy of a system. |
|
|
Intended to provide assurance related to the cybersecurity risk management program of an entity related to services or products. |
|
|
Intended to provide assurance related to the system used to produce, distribute, or manufacture goods, including commercial software. |
Based on the services and/or products provided by your vendor, your organization can request one or more of the above SOC reports best suited for its needs.
So how do you determine which one suits your needs?
Consider that SOC reports are intended to provide information for the purposes of assessing and managing risk. Therefore, your vendor’s SOC request should fit into your own broader risk management context. Only you can read the different SOC options and decide what you need from your relevant vendors, but we can tell you that your basis should be your own risk assessment and management processes.
After all, you may determine that SOC reporting is not necessary for certain vendors if your assessed level of risk for that vendor does not require a review of a SOC report from them.
- As such, your first step should be to determine the assessed level of risk for each relevant vendor.
- That risk level should help you prepare for the nature of the report you’ll get, as well as the timing you should expect.
- But it’s not just about the risk they pose—you’ll also need to determine any residual risk that you’re willing to accept.
- Then, you’ll be empowered to take appropriate action to manage that risk (e.g., additional due diligence of your vendor).
Once you’ve decided which report you need from your vendor(s), of course you’ll then need to ask them for it.
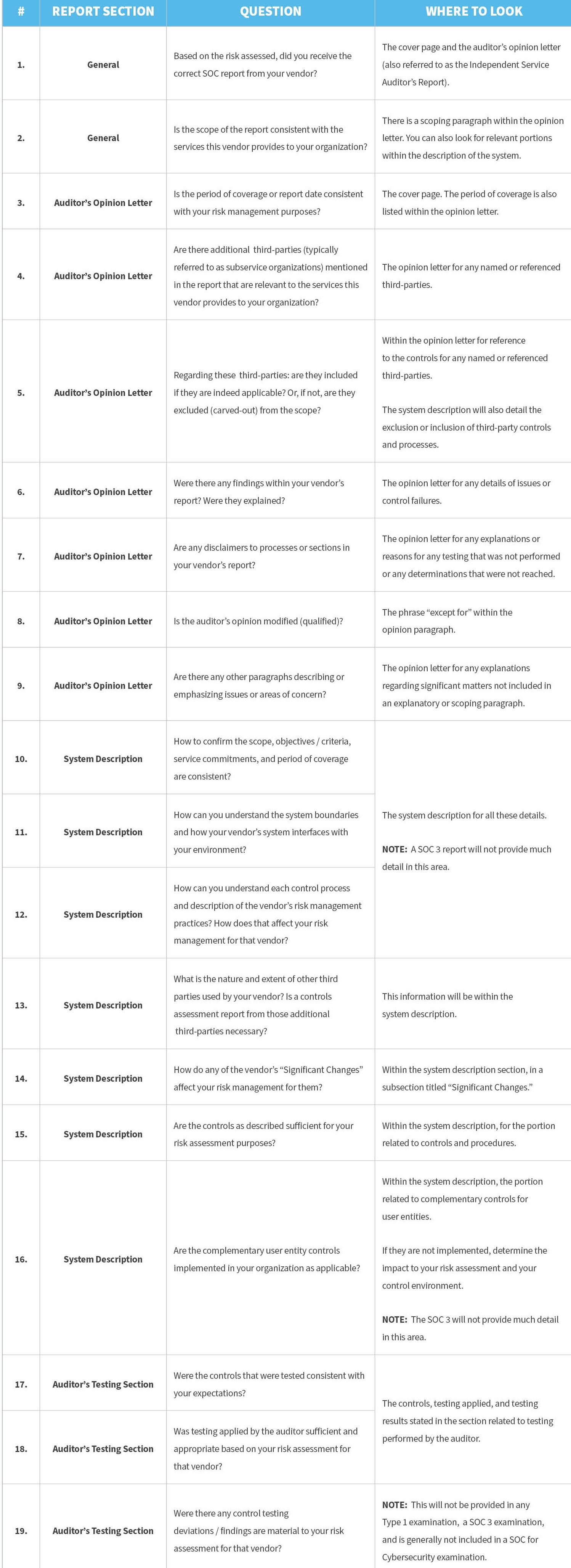
What to Look For When Reviewing Your Vendor’s SOC Report
But when you do have that full report in hand, there are specific places you’ll need to look in order to ensure the information is suitable for your needs.
The checklist below is intended to provide general guidance to ensure you get some key questions answered regarding your vendor’s SOC examination.
Ready to Request Your Vendor’s SOC Report?
Just like it was Uncle Ben that bestowed that bit of wisdom upon his superpowered nephew, we’ve now told you the same. As an independent third party that performs these audits for all sorts of organizations, we want to help you protect your organization as much as possible.
We know that when it comes to SOC compliance, the responsibility part may have been obvious, but it’s important that you now understand your additional power to expect it from others too, as well as how to find and wield the information you receive to maximize your security.
As you proceed in getting back your choice of SOC report from your vendor(s), you should also understand how to take full advantage of your own. Check out our content on the subject—including preparing for your next assessment and possible bridges to other standards—so that you’re ready for the next step SOC-wise, no matter what it is:
About Ryan Buckner
Ryan Buckner is a Principal and Chief Knowledge Officer at Schellman. Ryan currently serves on Schellman’s attestation leadership team and leads the firm-wide research and development for attestation methodology. Ryan is a CIPP, CISSP, CISA, ISO 27001 Lead auditor, and maintains multiple CPA licenses, among other certifications. Ryan is also an AICPA-approved and nationally listed Peer Review Specialist for SOC examinations. Having directly performed and completed over 1,000 service audits, Ryan is one of the most experienced service auditors in the world.




