Are Information Technology General Controls (ITGCs) Important?
Published: Jun 28, 2022
Last Updated: Oct 20, 2023
Did you know that, though its current official length is 5,500 miles, the Great Wall of China is estimated to have originally been 13,170 miles long?
Given that it was constructed during the 7th and 8th centuries, it represents an enormous engineering accomplishment. Built block by block, the Wall was commissioned by the Chinese emperor to protect his country from invasions, and it remains standing today.
If you were to compare your compliance foundation, would it be similarly lasting and fortified?
In an ever-evolving business world, you’ve likely had opportunities to automate systems and processes. That kind of progress is desirable, not only to improve efficiency from an operations perspective but to also bring a more enjoyable and seamless experience to your service customers and business partners.
These changes will not only need to be accounted for within your ongoing compliance projects, but you’ll also need to shore up any cracks in your foundational basis to remain best protected against risk.
We call these building blocks Information Technology General Controls (ITGCs), and in this article, we’ll detail what these are and how they fit into your overall “Great Wall” of protection.
You’ll learn why it’s important to remember these technological basics so that you take everything into account whenever improving on existing processes or implementing new ones, putting yourself in the best position for compliance moving forward.
What are ITGCs?
When we talk about ITGCs, these are the controls that are relevant for all areas of your organization and they involve processes, people, and technology—anything that supports or protects your business functions could be considered an ITGC.
These are the things that allow you to limit access privileges—they help you prevent issues such as unauthorized personnel retrieving sensitive information or virus damage to your system.
And though they’re all-encompassing, we can split ITGCs into a few categories:
- Physical and Environmental Security
- Examples include closed-circuit video cameras, temperature controls, keypads, or biometric access technology.
- Information Security:
- Examples include intrusion detection systems (IDSs), intrusion protection systems (IPSs), antivirus software, or encryption.
- Logical Security:
- These controls protect access levels. Examples include passwords or multi-factor authentication.
- Change Management:
- Controls that ensure only authorized changes are made to your environment. Examples of said changes include bug fixes or patching, as well as implementation of new features or system upgrades.
- Incident Response:
- Your multi-step processes that are in place to alert and mitigate interruptions or reductions to a service.
- Backup and Recovery:
- These mechanisms you have in place could be cloud-based on on-premise.
Whatever array of ITGCs you choose to deploy, they govern the way everything works together to support your organization’s operations and data protection.
How ITGCs Fit Into Your Organization
That’s a formal way of saying they’re your bread and butter. But let’s take it a step further and illustrate how it all fits together.
We’re leaving the Great Wall of China behind for now—think of your organization as a building. Your key business process control objectives—both manual and automated—would serve as the top (roof) of your structure.
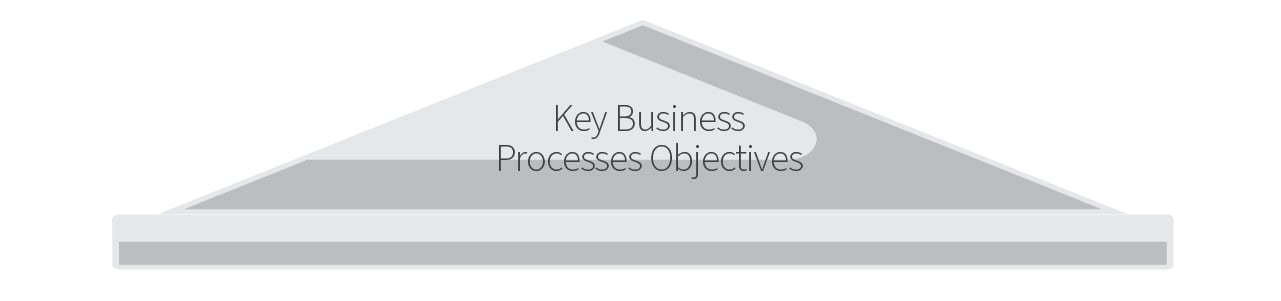
They’re objectives, so these are the desired outcomes your clients are expecting to be achieved in support of their financial processes and control environment—hence this “roof over their head” analogy.
And just as a roof rests on top of a support structure, so too do these objectives—their achievement must be facilitated somehow. And they are through your business process controls—a.k.a. the “structural beams” seen here—that represent the pillars of your manual and automated control environment.
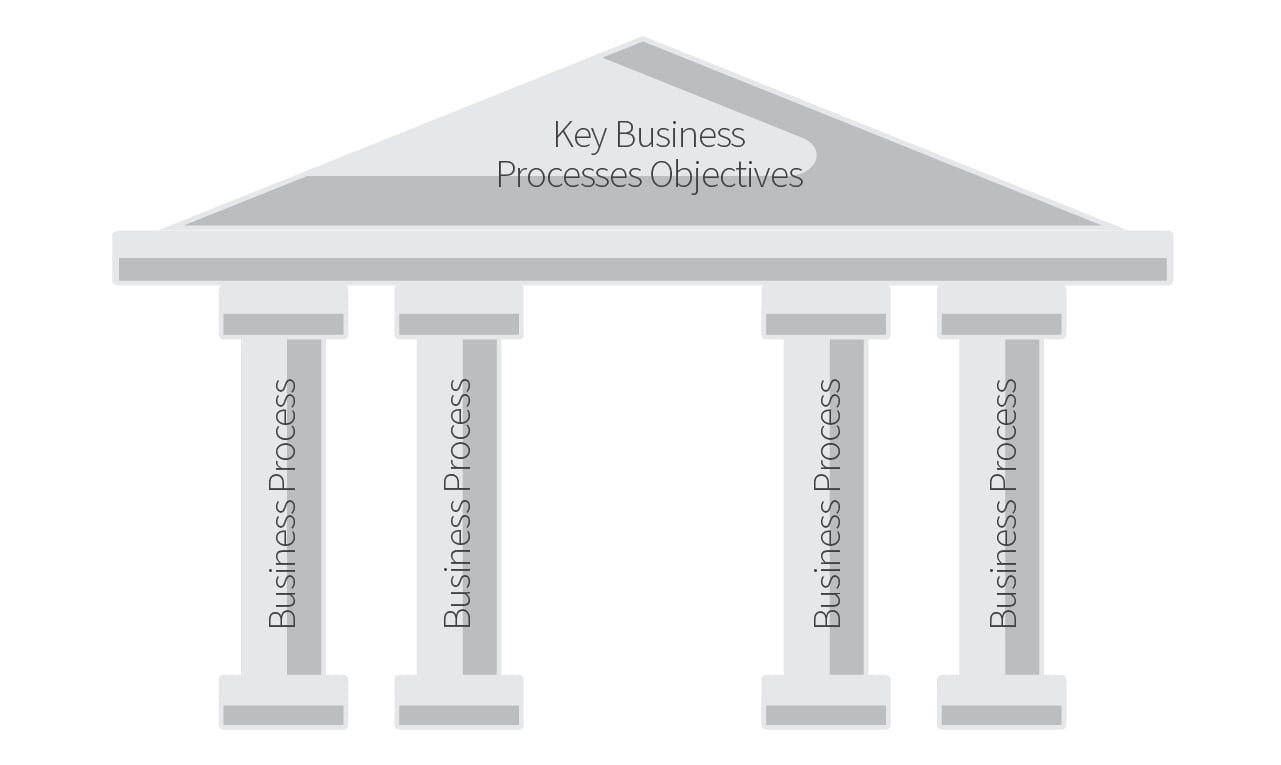
These controls help streamline and strengthen your key business processes that deliver your services to your customers. It makes sense that these support structures would demand a lot of your consistent attention to maintain and develop.
However, those support pillars alone are not sufficient to ensure that the key business process control objectives are achieved. Just as you do with a home, you need a strong foundation—this is where your ITGCs come in.
Your organizational foundation—the way you set up everything to work—is made up of primary or key ITGCs. These commonly include logical, environmental, and physical security to infrastructure—including the network, operating system, database, and application software levels—system change management, incident response, and backup/recovery.
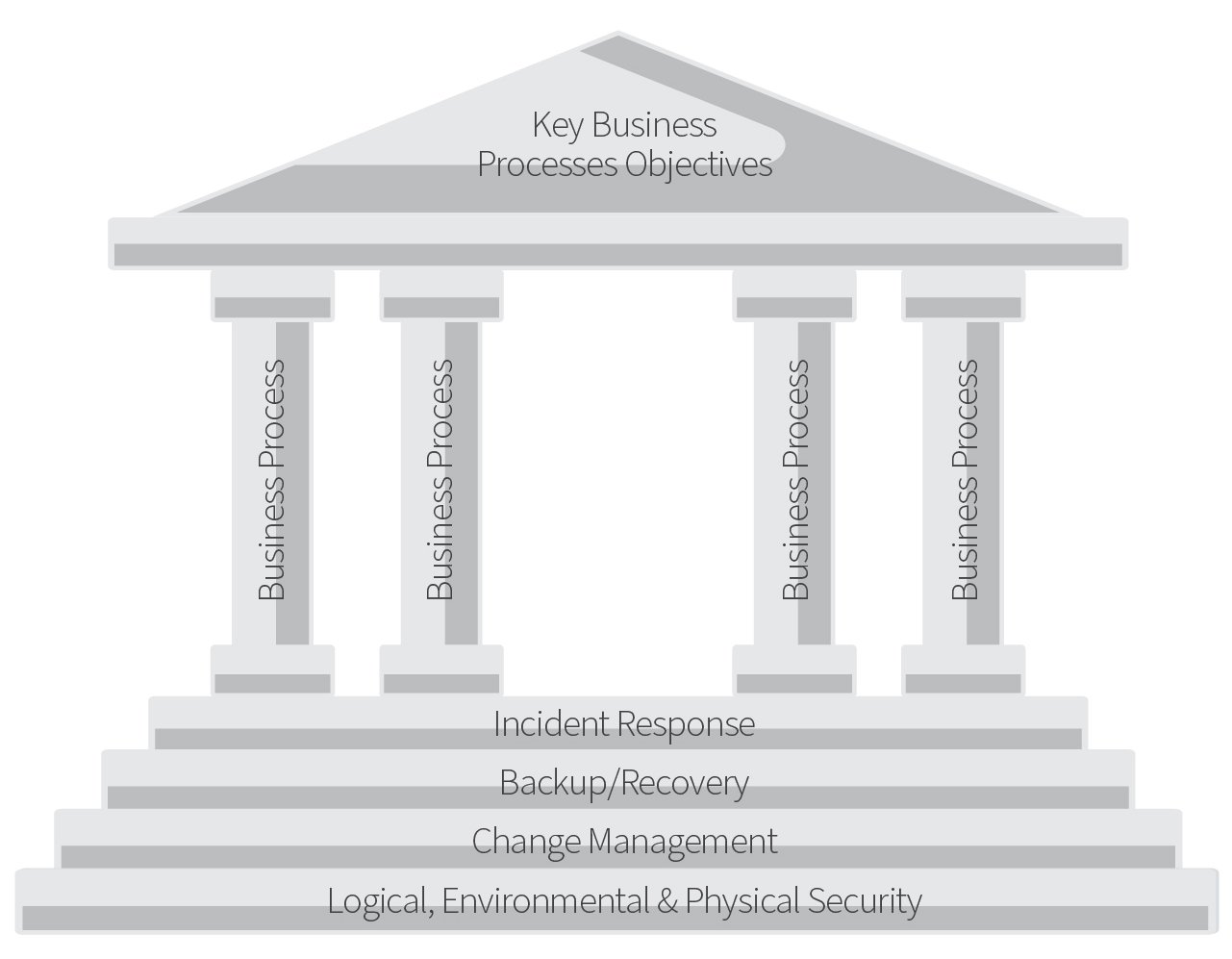
Back when you designed these controls, you likely took great care because of their strong influence on your organization’s daily operations.
But that was then.
In the excitement of new products and development of your business—likely around your product or services, other the things that will make you money and garner prestige—it can be easy to forget how those changes or improvements might also affect that underlying foundation.
Just as your home needs a level and solid foundation to keep everything upright, you can’t neglect the technological bedrock that supports everything you have in place. Because if you did—if during the development and upgrade to your business processes—your foundation was to become vulnerable, weak, and ineffective, you’d likely fail in delivering your objectives.
Those pillars supporting the metaphorical “roof” of your organization would begin to give way and ultimately cause the structure to collapse.
(Upgrading to hardwood floors doesn’t mean much if your foundation is cracked.)
How to Maintain Your ITGCs
Knowing all that now, it follows that to truly maintain a strong and effective structure, you must always keep all interrelated components in mind—both business and those supporting IT functions.
You set this bedrock long ago. Just as a house settles over time, creating imperfections in its foundation, so does your ever-changing landscape of technology and security. That’s why you need to take steps to ensure ongoing inspection is happening to account for and mitigate any cracks:
- Establish (or maintain) well-planned monitoring processes.
- These could be either internal or external but should include a risk assessment that aligns with your overall business objectives.
- Properly design and execute self-assessments and external evaluations.
- Consistently following through on these can help identify process improvements and unnoticed process breakdowns while also allowing management to develop a plan to mitigate against or remediate noted exposures. When self-assessing:
- Establish your assessment scope
- Identify critical or key controls that meet the organization’s objective(s),
- Analyze and evaluate how the control(s) is designed and its operating effectiveness,
- Remediate (if necessary); and
- Continue to monitor and review for control assurance.
- If you’re looking for something external, this could include, but is not limited to, third-party vulnerability scans, penetration testing, SOC 1 / SOC 2 reports, or an Agreed Upon Procedure for a control assessment
- Consistently following through on these can help identify process improvements and unnoticed process breakdowns while also allowing management to develop a plan to mitigate against or remediate noted exposures. When self-assessing:
- If you don’t have one already, establish an organizational structure responsible for policies and procedures related to ITGCs.
- Should you be so inclined, there are even software packages that can monitor ITGCs in real-time.
Ongoing Considerations for Your ITGCs
Your organization is running a business in full swing—its IT environment is likely very dynamic. Now you understand that as the technologies you use and the things that facilitate your products and services change, the same attention should be paid to the groundwork that supports them.
In ensuring that, you’ll avoid any potential fallout from cracks in your foundation and keep your “house” upright and functioning properly. That way, when it comes time for external assessments, such as SOC 1 or SOC 2 examinations, you’ll be less likely to turn up any surprises.
For more insight that can help inform you for future SOC examinations, read our other content that will simplify a few other basic concepts:
About Schellman
Schellman is a leading provider of attestation and compliance services. We are the only company in the world that is a CPA firm, a globally licensed PCI Qualified Security Assessor, an ISO Certification Body, HITRUST CSF Assessor, a FedRAMP 3PAO, and most recently, an APEC Accountability Agent. Renowned for expertise tempered by practical experience, Schellman's professionals provide superior client service balanced by steadfast independence. Our approach builds successful, long-term relationships and allows our clients to achieve multiple compliance objectives through a single third-party assessor.



