HITRUST and The Effect of TEFCA
Published: Oct 19, 2022
Last Updated: Aug 11, 2023
American journalist Sydney J. Harris once said that “the two words 'information' and 'communication' are often used interchangeably, but they signify quite different things. Information is giving out; communication is getting through.”
Mr. Harris died in 1986, well before the digital age took off, but that sentiment proved remarkably prescient. Because even though these days, most sectors have embraced the connectivity technology can provide, it’s still not always easy to communicate information easily and efficiently.
Look no further than healthcare, which, like other industries, has gone largely digital, as has the exchange of health information.
But think about it: when you’re faced with an unexpected medical event, who’s got what access to your digital health information is likely the last thing on your mind. You—like most patients everywhere—assume your medical records are securely guarded, standing at the ready in some vast medical database, just waiting to be called upon by your latest attending medical professional.
For the most part, those assumptions would be correct. But that doesn’t mean it’s been easy behind the scenes.
Schellman has provided healthcare compliance services for over 15 years now—we’ve helped organizations stay within regulations as they’ve adapted to this changing landscape, and now we want to provide insight on one of the latest updates and its ripple effect.
In this article, we’re going to briefly track the present difficulties within health information exchanges (HIEs) before we get into how the new and final version of the Trusted Exchange Framework (TEF): Principals for Trusted Exchange aims to change that through HITRUST.
Understanding this upcoming shift will help you prepare for any incoming requirements—whether that means HITRUST certification or not.
What are Health Information Exchanges?
Back in 2009, the push to digitize medical records was formalized with the passage of The Health Information Technology for Economic and Clinical Health (HITECH) Act. Amidst this shift to digital, HIEs—the digital networks by which protected health information (PHI) is shared—have become more common.
HIEs are what allow the physicians from your emergency room visit to access medical records from your primary care provider in a different health system. Access to such information can make all the difference in an emergency, but only if it is available in the right place at the right time.
But despite all the progress in the time since HITECH, HIEs are still limited in reach. Exchanges typically only cover areas mandated by regulation—areas such as states or hospital systems that operate in close geographic proximity with significant patient overlap. And while standards for tagging patient medical data are often established within a network, these are different between HIEs—the inconsistencies make it difficult to share medical records effectively and efficiently.
So, while you may assume that your medical history would be seamlessly available to any provider who needs it, its actual availability largely depends on the exchanges each provider uses.
What is the Cures Act?
But the passage of the 21st Century Cures Act (Cures Act) in 2016 aimed to solve these challenges. It directed the National Coordinator to “develop or support a trusted exchange framework, including a common agreement among health information networks nationally” in hopes that central coordination would connect isolated exchanges into a network of networks.
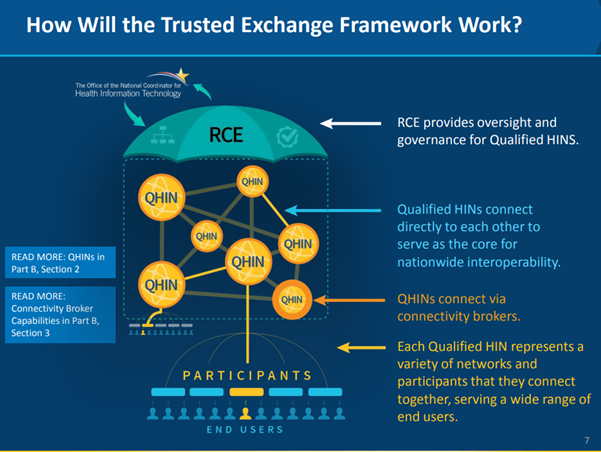
To that end, the Office of the National Coordinator (ONC) awarded a cooperative agreement to The Sequoia Project, a Virginia-based non-profit. The organization now serves as the Recognized Coordinating Entity (RCE) responsible for developing, updating, implementing, and maintaining the Common Agreement (CA).
What is the Trusted Exchange Framework?
Working in combination with the CA is the Trusted Exchange Framework (TEF): Principals for Trusted Exchange, the final version of which was released by the ONC in January 2022. The TEF describes a common set of non-binding, foundational principles for trust policies and practices that can help facilitate exchange among health information networks (HINs) (which contain HIEs).
Together, TEF and CA are now the foundation for the establishment of Qualified Health Information Networks (QHIN)—the building blocks of a national, secure information exchange. The framework has been operational as of October 3, 2022.
Health Information Networks Need HITRUST
But to become part of this greater network—to become a QHIN—and make sharing health information easier, you must prove your security safeguards for that information. To that end, the CA contains a set of security requirements outlined in section 12.1.
More specifically, section 12.1.2 of the Common Agreement requires QHINs to achieve and maintain a third-party certification from an industry-recognized cybersecurity framework—currently, the HITRUST r2 Validated Assessment is the only certification that complies with section 12.1.2.
For its part, HITRUST is already actively certifying potential QHINs. Future applicants to be QHINs must provide:
- Evidence of certification at the time of application; or
- Commitment that certification will be achieved within twelve (12) months of application acceptance.
But it’s not just the QHIN itself that must make necessary security moves—the CA also outlines certain flow-down requirements that QHIN participants and sub-participants must meet. Although the RCE does not explicitly require participants and sub-participants to formally become HITRUST certified, their requirements are identical to those for QHINs who are obligated to undergo certification for that same purpose.
These requirements include:
- Appropriate security control implementation;
- Compliance with the HIPAA Security Rule provisions (if a non-HIPAA entity); and
- Specific restrictions on TEFCA information used outside the United States.
At the very least, QHINs must include these requirements in their participant agreements and also mandate that their participants also include them in any sub-participant agreements. Whether the participants and sub-participants do choose to get HITRUST certified or not, the responsibility to verify their compliance with the requirements ultimately lies with each QHIN.
Do You Need to Get HITRUST Certified?
There’s no denying that this new foundational framework TEFCA will stir up change within the healthcare industry in its attempts to make the communication of information easier but no less secure. As the only acceptable compliance initiative that meets these requirements (currently), HITRUST certification will play a big role to start.
In fact, it eventually may play an even bigger one, because while at the moment it’s only requisite for QHINs, it’s anticipated that at least some of these networks will follow suit with the RCE and soon require a HITRUST certification from their participants and sub-participants as well.
That means that wider HITRUST adoption is likely on the way, and if you’re an organization that deals with healthcare information, you may need to look into this certification. To get you started, check out our content on the subject:
- What is HITRUST Certification?
- How to Scope Your HITRUST Assessment: 5 Components to Consider
- Do You Need a HITRUST External Assessor?
The Sequoia Project is currently accepting QHIN applications, and more information is expected to become available as QHIN applicants complete that process. But in the meantime, should you have any questions, please feel free to contact us—as HITRUST external assessors for a number of years, we are ready to alleviate any concerns you may have.
About Michael Seegel
Michael Seegel is a Senior Manager with Schellman. Prior to joining Schellman in August 2018, Michael worked as an IT Audit Manager, specializing in managing SOC 1 & 2 Type II engagements. Michael also has prior experience performing HITRUST assessments, ISO 27002 audits, IT SOX compliance, and ERP implementations. As a manager at Schellman, Michael primarily focuses on performing HITRUST assessments for organizations in or doing business with healthcare organizations. Michael currently holds the CPA, CISSP, CISA, and CCSFP certifications.