What is HITRUST Certification?
Published: Aug 30, 2022
Last Updated: Oct 19, 2023
Ernest Hemingway once said, “the best way to find out if you can trust somebody is to trust them.”
The man may have been a legendary novelist, but his time was well before that of compliance. You can guess what would happen if you asked your customers to just “trust you”—they’d likely consider taking their business elsewhere.
But luckily, these days you have plenty of options to obtain third-party validation of your environment, systems, or services—you just need to ensure you choose the right one for your purposes.
For those of you who need to demonstrate accordance with HIPAA, you should read on to learn more about one said option.
It’s called a HITRUST certification, and you can leverage one to show compliance with a security and privacy controls framework that includes HIPAA.
This is an entirely separate endeavor from a HIPAA attestation, which is why we’re going to detail exactly what HITRUST is in this article.
You’ll learn why this certification exists, what it does, and how it works. As you’ll soon learn, HITRUST isn’t simple. But after reading, you’ll understand it a bit better as you consider your compliance options.
Who Can Use HITRUST Certification?
Historically, the HITRUST Certification arose due to the lack of a certification standard for HIPAA. As a security and privacy certification in the healthcare space, HITRUST can support those organizations who seek to be “HIPAA certified.” If you’re a covered entity—hospitals, insurers, etc.—who want confirmation that your vendors can handle sensitive healthcare data (protected health information) properly, this certification can also help you.
However, it may have been generally focused on the healthcare industry in the beginning, but HITRUST has since become an agnostic framework that champions safeguarding sensitive information and managing information risk for global organizations across all industries and throughout the third-party supply chain.
Through a set of products and tools that provide an integrated approach to aligning, maintaining and supporting an organization’s information risk management and compliance objectives, HITRUST can meet the challenges of assembling and maintaining the many and varied programs needed to manage information risk and compliance through an established framework.
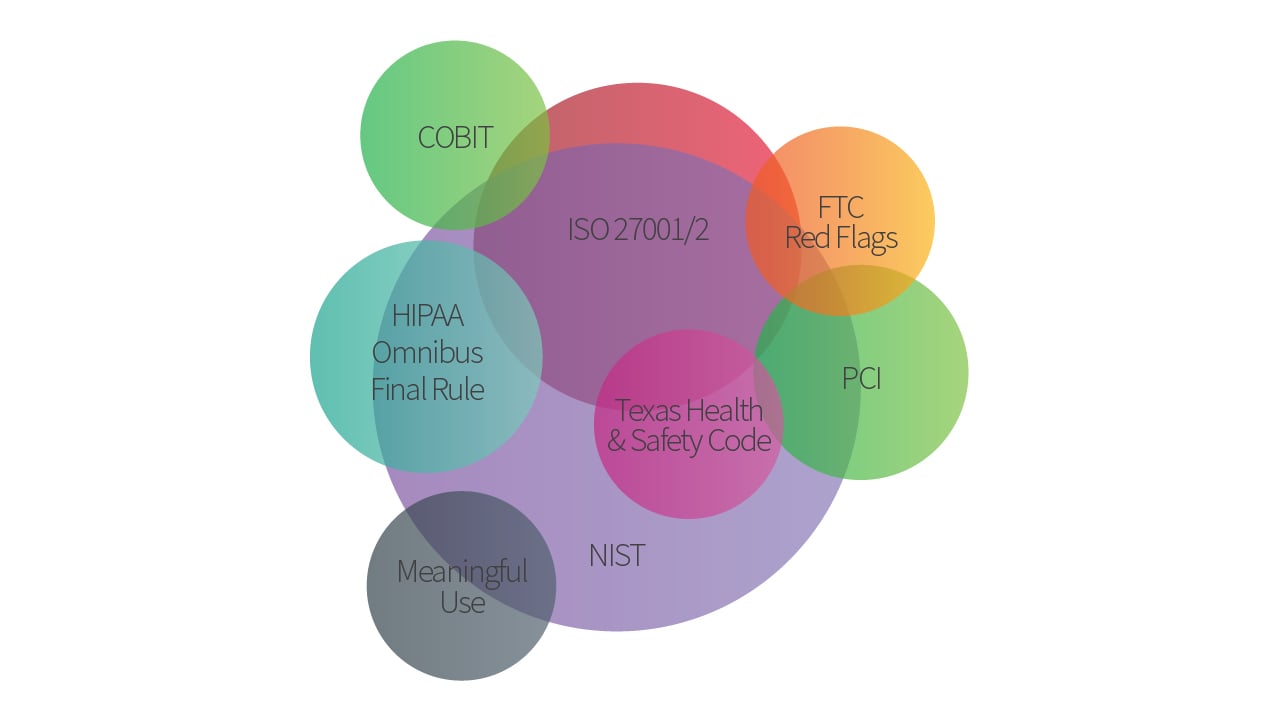
Called CSF, the HITRUST framework is a blend of existing standards—including HIPAA, NIST, and ISO 27001—into one holistic security framework. As HITRUST has grown, it continues to branch out beyond just the healthcare space. Because its CSF program focuses on overarching security and privacy principles, HITRUST can apply to any organization.

How Does HITRUST Certification Work?
A HITRUST-approved External Assessor will provide trained resources to gauge compliance with security control requirements and document corrective action plans that align with the HITRUST CSF framework.
But how does that work?
HITRUST offers two forms of certification, called the HITRUST Implemented, 1-year (i1) Validated Assessment + Certification and the HITRUST Risk=based, 2-year (r2) Validated Assessment + Certification.:
- HITRUST i1 certification uses a static set of control requirements that you would be tested against.
- As the full name implies, this certification is valid for one year from the date listed on your actual certificate.
- HITRUST r2 certification uses a varying set of control requirements driven by responses to pre-defined HITRUST scoping factors (e.g. how many records are held).
- As the full name implies, this certification is valid for two years from the date listed on your actual certificate.
What is HITRUST i1 Certification?
That static set of requirements that doesn’t vary from organization to organization implies that this route is more streamlined than the other. But the HITRUST i1 also only focuses on testing whether each control requirement has been implemented.
That makes it important to understand what HITRUST means by “implemented.”
- It must be demonstrated, through evidence, that a given control requirement has been designed and is operating effectively. (Similar to the validation of a control for a Type 2 SOC 2 examination).
- Through that evidence, you must prove to your external assessor that you deserve a certain score for each control requirement as relates to “implementation.”
- The i1 currently has 219 of these control requirements total, which are divided into 19 areas of testing (called “domains”).
- Think of each of the 19 domains as mini-tests, each requiring a passing score for the organization to achieve certification of your in-scope system(s). (The 219 control requirements are not evenly split out across the 19 domains, so some tests are quite mini while others are not so mini.)
- If you fail even one of the 19 mini-tests, your ability to be HITRUST certified is off the table.
Everything relies on the aforementioned scoring, which is driven by what percentage of the control requirement statement validates that the organization has implemented the components of the requirement.
For an i1 assessment, your auditor will evaluate your evidence and give each control requirement an implementation score of 0, 25, 50, 75, or 100 percent. The average of your percentages must be at 83% or above for each domain to pass.
Illustrating HITRUST i1 Scoring
To further illustrate the scoring, let’s take one of control requirements within the domain called “Endpoint Protection.” This particular requirement reads as follows:
- “The organization configures malicious code and spam protection mechanisms to
- perform periodic scans of the information system according to organization guidelines;
- perform real-time scans of files from external sources at endpoints and network entry/exit points as the files are downloaded, opened, or executed in accordance with organizational security policy; and,
- block malicious code, quarantine malicious code, or send an alert to the administrator in response to malicious code detection.”
There are three very specific components needed here. If you’ve implemented two of the three components for the in-scope environment, that equates to 66%. We noted before that the scoring is only in 25% increments, so a 66% would be rounded up to 75%.
This is just one control requirement of the 8 total in “Endpoint Protection” domain. If we assume you scored 100% on the other seven, averaging all the scores together ([75+100+100+100+100+100+100+100] / 8) would indicate a domain score of 96.875.
That’s above the required passing score for each domain of 83 or above, so you would still pass this one even with a gap for one of the requirements.
What is HITRUST r2 Certification?
When you consider the HITRUST r2 certification then, it contains the same 19 domain areas (“mini-tests”). Unlike the i1, the total number of control requirements split amongst the 19 domains within r2 varies based on predefined risk factor questions answered during the r2 assessment.
Given the depth of these questions, we’ve written an entirely separate blog on HITRUST scoping and all the potential risk factor inquiries you might have to answer. You can read that article for the full specifics, but you can expect at least one to be regarding the number of records your in-scope system handles. (To answer, you’ll have to choose from three options: 0 to 10 million, 10 to 60 million, and over 60 million records.)
And while the i1 only looks at “implementation,” the r2 certification looks at the full control maturity model. That includes policy (worth 15%), procedure (worth 20%), implemented (worth 40%), measured (worth 10%), and managed (worth 15%)).
For the r2, the average score across the control requirements in any of the 19 domains must be 62 or above to achieve certification. Though these scores may include corrective action plans associated with the certification, your eyes still may have popped at such a lower acceptable percentage when compared to the i1.
But there is a caveat.
For the categories of measured and managed, it’s generally required to have a completely independent person or group assess those control requirement performances:
- A score of 25% can be achieved through an operational measure performed by the same person or group responsible for the control/requirement being measured.
- However, if you’re seeking a score above 25%, you’ll need the person or group assessing those performances to be independent, as in separate from the users who perform the control, and they should conduct their evaluations of these categories on an ongoing and periodic basis.
Hence, most organizations don’t score themselves in measured and managed, and so the top possible score (across policy, procedure, and implemented) is 75%.
Next Steps for Your HITRUST Certification
Ernest Hemingway might’ve asked your customers to just trust you, but you can do better than that. HITRUST makes for an attractive option to do so, particularly for those with HIPAA obligations. But now that you understand more about the framework and certification process, you know that HITRUST’s CSF program can help any organization as well.
You’re likely still considering all the possibilities when it comes to what suits your organization’s needs. As such, you should read our other content regarding HITRUST so you can determine more easily if it’s the route for you:
When making your decision, you may prefer to talk things out directly regarding your organizational specifics. If that’s the case, please also feel free to contact us. We’d be happy to set up a conversation to further deconstruct HITRUST and whether or not there’s a place for this certification in your portfolio.
About Ryan Meehan
Ryan is a Senior Manager at Schellman. He has worked in public accounting since 2007 specializing in compliance auditing, including SOC examinations, ISO certifications, and healthcare audits such as HIPAA and HITRUST. Ryan has serviced clients in a multitude of industries including business process outsourcing, financial services, information technology, and healthcare. Ryan holds certifications including the CISSP, CISA, ISO 27001 Lead Auditor, CIPP/US, CCSFP, and the Advanced SOC certification.




